Have you ever thought about how different apps and devices connect to each other, from the car that tells you where the nearest gas station is, to your phone that gets weather and sports updates? The unsung hero of our connected world is the Application Programming Interface (API). They are the connective tissue that enable developers to explore new services, integrating them into new, great solutions faster. The power, flexibility and widespread use of APIs makes it essential that the way users interact with them is secured.
To accomplish this, developers can use one of several authentication standards including API Keys, OAuth, and Java Web Tokens (JWT). In this article we will look at what an API key is, the risks of exposing them and recommendations for API key protection best practices.
What are API Keys?
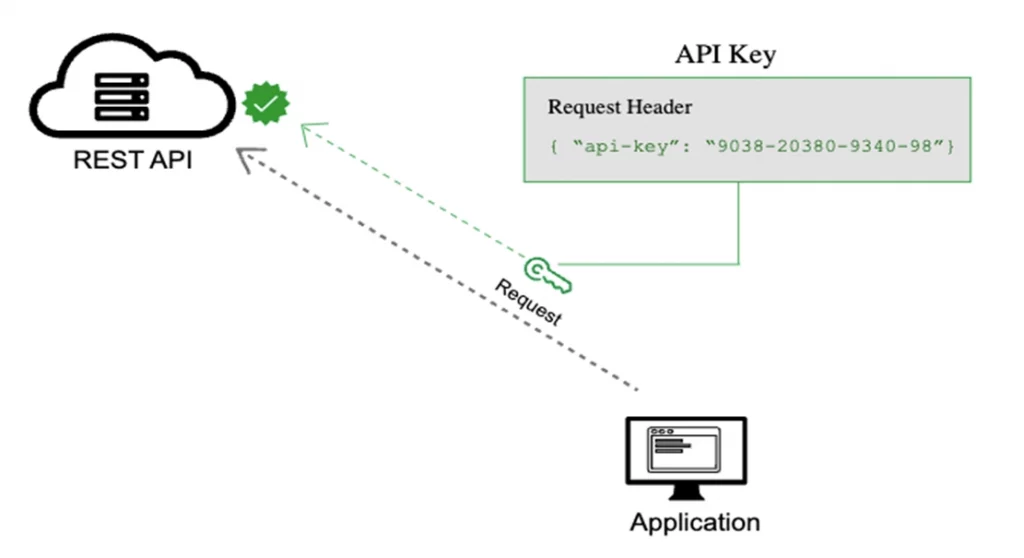
An API key is used as a form of authentication to provide users with authorized access to the data it returns. The authentication access is provided in the form of a secret token. In simple words, an API key is akin to a password that lets the API confirm your identity. Once an API knows you are legitimate, you can access the application full set of features.
Example of an API key: 3f4ea49s-c113-471t-a573-q9r005yrb52fe
Risks and Consequences of API Keys Exposure
Now, consider an unauthorized attacker gets authenticated to an API. This means the attacker can see all the information provided by the API. The attacker can then modify and update all the information – files, workflows, contacts, pipelines – related to the API. In a real-world example, cybercriminals have been observed exploiting (poorly protected) cryptocurrency exchange API keys and using them to steal cryptocurrencies from victims.

Common API Key Protection Errors – The Importance of Secured API Keys
An insecure API key is a high-value target for attackers who can use them to obtain critical data and gain unauthorized access to computers and networks. They are often targeted by distributed denial-of-service (DDoS), man-in-the-middle (MITM) attacks, and broken access control, which means they need to be exceptionally secure. A review of several recent high-profile security incidents highlights the challenges in protecting API keys.
- Publicly exposed without a password: An API key owned by Starbucks was found online without password protection, which could have been exploited by attackers to access internal systems and alter the list of approved users of their application.
- Poor API coding practices: Researchers recently found 3,207 apps were exposing the API keys that were linked to Twitter accounts. In this case, developers may have embedded the keys in the Twitter API but forgot to remove them prior to production. Researchers confirm that the leaked keys would allow attackers to access Twitter accounts directly and perform a range of actions such as read direct messages, retweet, like and delete tweets, modify, add, and change the access account settings.
- Hard-coded API keys: In another possible example of developer error, hard-coded API keys at HubSpot exposed over 1.6 million names, email addresses, and contact numbers. Given the speed of app development and updates, developers often hardcode API keys into their source code, accelerating development, but also making it easy for attackers to obtain sensitive information.
As API usage continues to soar, the risk of API key related security incidents are sure to follow, resulting in data loss, fraud, and business disruption.
API Key Protection Best Practices
There is no single step an organization can take to make sure their API keys are protected. Improving your API key protection posture requires a collaborative effort that includes developers, application owners and the security team.
- API key management: A critical step to ensuring API keys are protected is to implement an API key management program, which can help minimize some of the risks mentioned above. For example, applying expiration dates to API keys can help minimize the impact of the discovery of a hard-coded API key. Similarly, key management would allow an organization to quickly invalidate the API keys in the event of a compromise or breach.
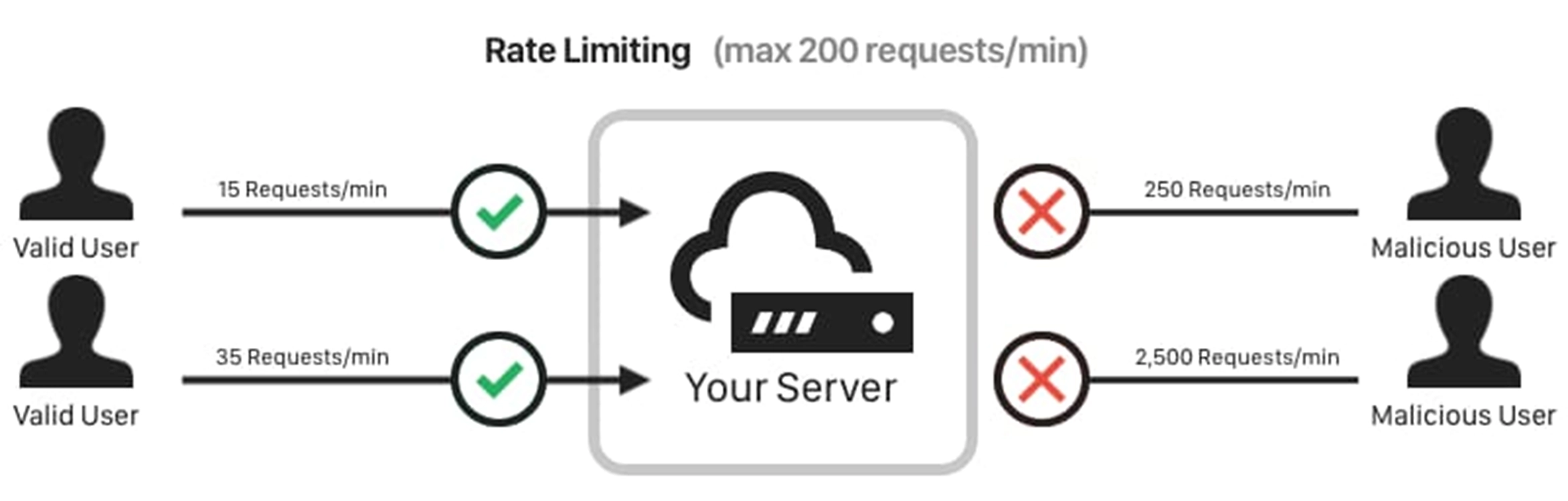
- Rate limiting API keys: Rate limiting your API keeps it from being overloaded in the case that an attacker succeeds in bypassing your encrypted authentication and authorization procedures. For example, an unusually high number of requests from a user may be an indication of malicious activity in the form of a denial-of-service assault. A rate limiting and monitoring solution keeps the API keys secured and in turn the API service healthy.
- User authentication: For the simplest degree of protection against the attackers, you must be aware of who is using your API. As a result, users must be registered by giving them API keys. Assigning API keys to enforce simple authentication enables you to control who is using your API. It also allows you to monitor, and determine who is making API requests.
- Train developers on secure API coding practices: APIs function a bit differently than a traditional application because they tend to include the desired function and the payload/content, which may include sensitive data and access to API keys. It’s critical that developers be trained to understand these subtle differences and account for them in their coding efforts.
- Adopt an API specification framework: Complementing the developer training effort is an adoption of an API specification framework like OpenAPI. Doing so helps ensure that the API is coded to the defined specification, which would include how API keys are treated and used. Specification frameworks provide the additional benefit of improving quality, consistency, and overall security.
Summary: Stay On Top of Your API Security
API keys, when implemented correctly, are a great way to enable authorized communication with different servers. As we reviewed in this article, there are numerous risks in leaving the API keys exposed which can be a great challenge to any organization. Therefore, API key security has become vitally important for businesses today. Thanks for reading.
Schedule your free API Security Assessment today.
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.




