Introduction
After winning numerous industry accolades and awards, we are very pleased to announce the latest feather in our cap, where Cequence was named a Best-in-Class API Security solution among all vendors by Datos Insights (formerly known as Aite-Novarica). The Datos Insights Vendor Evaluation is a comprehensive, proprietary process that is designed to provide a holistic analysis of participating vendors and identify market leaders in each evaluated vendor market. You are likely aware of similar reports such as the Gartner Magic Quadrant (MQ) and Forrester Wave. By incorporating many aspects of a vendor’s essential characteristics for success and growth, including financial and client stability, product features, and customer service, the vendor evaluation provides an actionable guide for market participants looking for viable third-party vendor solutions and services.
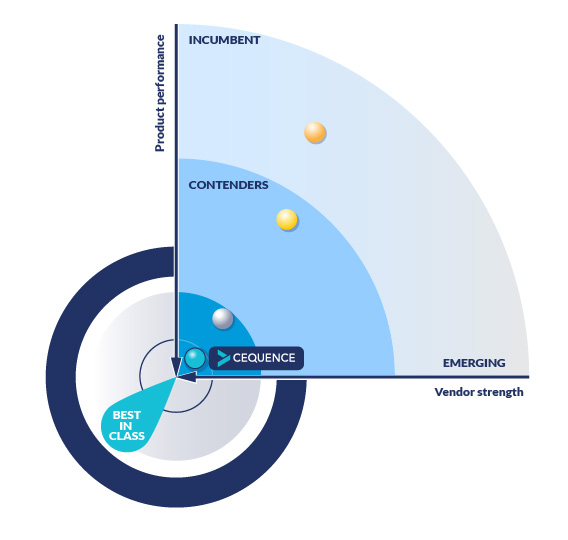
History Made: Highest-Ever Product Score
“The company has become one of the market’s most respected API security vendors.” This is the one-sentence summary Datos Insights offers about Cequence in this latest report, and this market designation is only bolstered by their in-depth analysis and consideration of the entire field of API security vendors. According to Datos Insights’ latest report, not only did Cequence earn the Best-in-class API Security designation and the highest position in the report, but it also earned “one of the highest product scores in the history of Datos Insights publishing its Vendor Evaluation reports”. This is a significant achievement that we have worked hard for and are proud to have earned.
So why should you read this report? This Datos Insights report should be required reading for every enterprise, not because it validates our technology and execution, but because it does an excellent job of educating us on the history, the dynamics, and the necessity of great API security. They offer a detailed breakdown of nearly every aspect of what such a solution could and should offer to effectively protect this massive attack surface – in fact the largest single attack surface for many enterprises.
Learn Why API Security Is Essential
Business productivity and customer interaction has come a long way as APIs have evolved over the last 20 years. Today, our businesses simply couldn’t operate (or compete) without the APIs that enable every aspect of enterprise operations. Malicious actors know this and work hard to take advantage of these tens of thousands of little windows into our critical infrastructure and sensitive data. The question becomes, how well have we closed, locked and protected these windows? To be sure that we have done a good job, we should understand all the different ways data could be accessed or lost. Datos offers the following graphic as a summary of the many threat types that we should be aware of and protect against.
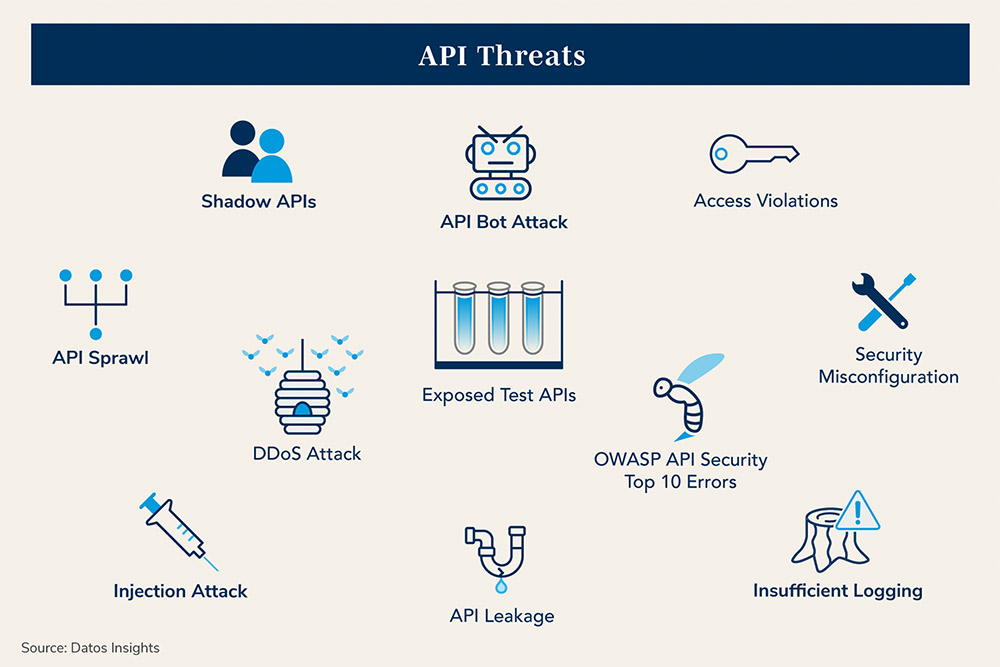
And not only are there many ways that APIs may be compromised, but the amount of damage from just a single breach can be enormous. In fact, a simple data scraping technique applied to a website API allowed the exposure of 700 million LinkedIn user records just 2 years ago. Many more complex attacks have also been successfully used to breach many millions of records every year, ranging from deliberate exploitation of zero-day vulnerabilities to benign negligence of out-of-date and insecure APIs. In fact, with the rapid development of new APIs, I am afraid that new vulnerabilities are unwittingly introduced into many environments almost every day.
While this is certainly educational, and good for any SecOps professional to understand, it is infinitely more important that your API Security solution effectively addresses every one of these avenues of threats and more.
Learn What API Security Can (Must) Do for You
We know that the landscape of APIs at most companies is extremely complex, and there is not a single person in any company who knows about every one that is in use or how it connects to other APIs, servers, and databases. So, there is a whole sequence of things that must happen to truly protect all your APIs. Datos Insights used a very thorough and rigorous process to dig into every aspect of these essential capabilities throughout the evaluation process. This is often referred to as API Protection Lifecycle and includes everything from discovery of APIs currently in production, to preemptive security integrated into the IDE and CI/CD pipelines, to active notification and protection of identified issues. Following are thirteen areas that Datos Insights drilled into in this report:
- Implementation Model
- API Discovery Capabilities
- API Security Policies
- Access Control
- API Inventory and Attack Surface
- Vulnerability Detection
- Threat Management
- Event Notification
- Monitoring
- Testing
- Dashboard
- Auditing
- Solution Design
I am pleased to report that Cequence achieved a positive mark in every single subcategory across all thirteen product areas, the only vendor to do so. Think, for example, about whether the implementation model and integration points of a solution map well to your own environment, both how it is today and how it may evolve into the future. The figure below shows a heat map of the results for Cequence. Please download the complete report for the full table.
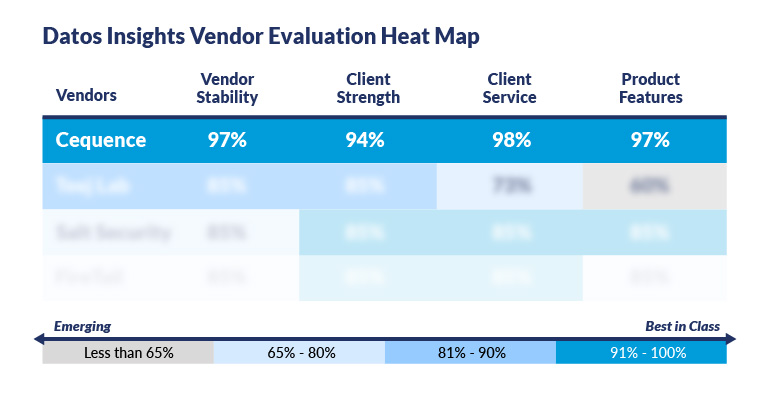 Partial Figure from the report
Partial Figure from the report
It is also important to note that the proprietary methodology developed by Datos is holistic and goes well beyond today’s product capabilities. This includes essential characteristics for success and growth that are also critical to customers in the long run, like financial stability, customer service and product roadmap. So, what will you learn about Cequence in this report?
Learn If Cequence Is the Best Vendor to Protect Your APIs
To earn the best-in-class API Security designation in the Datos Insights report, we had to prove beyond doubt that we can deliver everything today’s enterprises need to keep their businesses safe from threats, both malicious and benign, regardless of what the operating environment, geography, size or vertical is. We not only had to check boxes, but also prove by documentation, product demonstration and customer references that we could backup everything we claimed. Most of the vendors (including some very well-known public companies and “unicorns”) either did not make the cut or could not provide customer references. Whoever you ultimately choose to protect your APIs, know that you will be far better informed on that decision after reading this report.
Datos Insights has been in the vendor comparison business for nearly 20 years. The current Matrix methodology was launched in 2015 and has created nearly 70 reports, each requiring about six months and 400 hours (about 2 and a half weeks) of researchers, advisors, and editorial staff to produce. This means that companies looking to understand and evaluate possible vendors can feel confident in leveraging this trusted third-party effort to save a ton of time and move much more rapidly toward their best-informed decision. We thank the Datos Insights team and especially Tari Schreider for leading this research.
Conclusion
It is not enough for CISOs to simply check the API Security checkbox and move on. Feature additions in web application firewalls (WAFs) or extending the firepower of their API Gateways, for example, simply won’t cut it today or in the future. APIs are the single greatest software attack surface for most medium and large enterprises, and Datos Insights believes and demonstrates how standalone API solutions are essential to handle the complex API environments that are now so prevalent.
I highly recommend this Datos Insights Vendor Evaluation to anyone who is either just starting or continuing their exploration and evaluation of API security solutions.
Get Your Copy of this Datos Insights Report
To learn more on why Cequence was ranked the best-in-class API Security solution, download the full Datos Insights Vendor Evaluation: API Security Solutions.
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.





