Survey Highlights API Business Value and API Security Balancing Act
Much like the plumbing in our homes that works behind the scenes to make our lives easier, APIs are quietly helping organizations large and small generate significant business value APIs silently help us purchase nearly anything we need from our living room and have it delivered the next day. They are the glue that enables the apps we use to manage our money, automate our homes and keep them safe and secure. Factors driving the explosive use of APIs include cloud and microservices adoption, mobile device ubiquity, and the move to agile, more iterative development as a means of delivering more compelling new features to market more quickly.
The same characteristics that developers love about APIs are also leveraged by attackers as seen in recent API security incidents at Optus, Twitter and Telstra to name just a few. In response, security teams are using disparate solutions that lack integration, slowing attack detection response times which can result in a failure to provide adequate API protection from theft, fraud, and business disruption. These are just a few of the findings from a recent survey of 300 API security decision makers to explore how businesses are maximizing API business value, while maintaining and ensuring proper security.
APIs Help Drive Revenue
More than three quarters (79%) of the respondents stated that their revenue dependency on APIs would increase over the next 12 months. On the surface, this finding seems obvious given the use cases and trends mentioned above which are, in many ways, necessitated as the move towards an internet connected society continues.
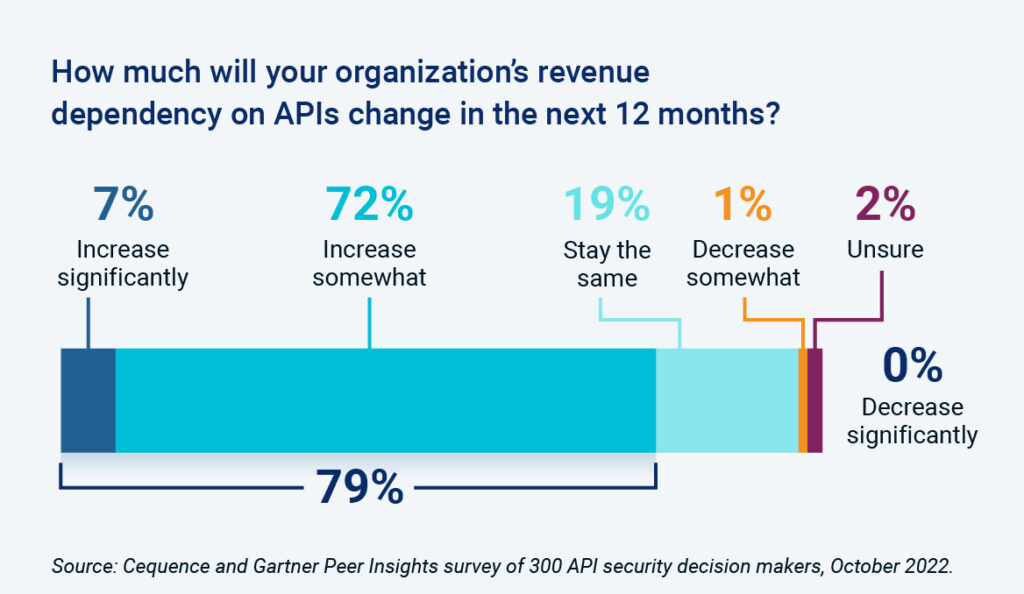
Drilling more deeply into specific API use cases shows that partner and third-party APIs are viewed as the most significant revenue drivers at 66% and 67% respectively. On the surface, this finding was surprising because partner and third-party APIs are not as obviously connected to revenue as one would think. The reality is very different. Third party and partner APIs are core to making our money management app seamlessly link multiple accounts together; they help simplify our shopping experience, either in-person or online, by providing up-to-date local inventory status or by validating our credit/gift cards behind the scenes. Viewed from this perspective, it would be easy to ask why the findings were so low. Clearly, APIs are viewed as a critical element in driving revenue and business value, which makes them a valuable target for attackers.
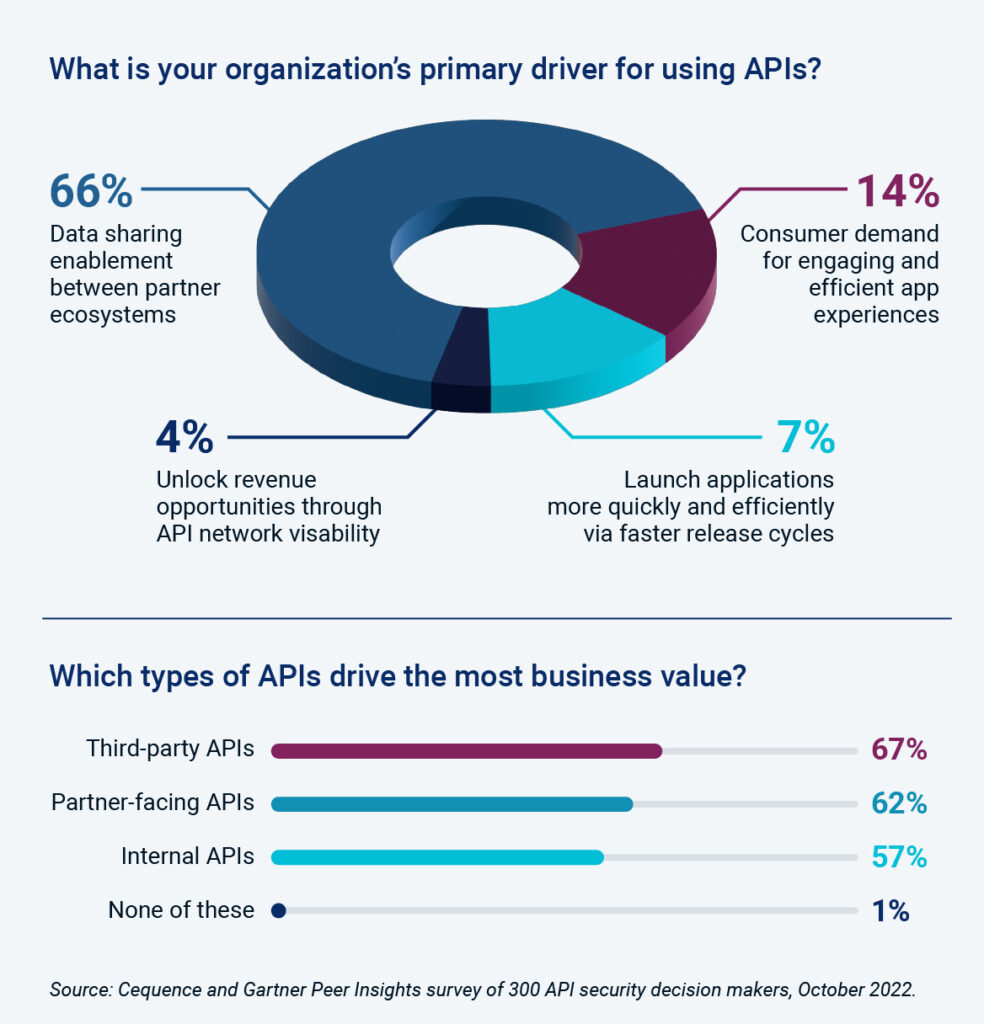
Data validates API Business Value Jeopardized by Disparate API Security
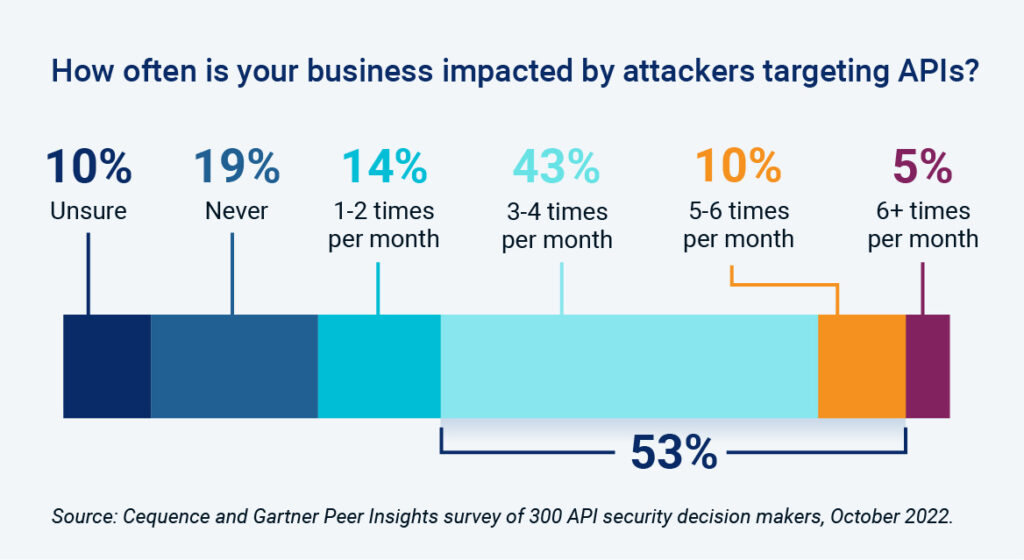
Surprisingly, the survey showed that more than half (53%) of the respondents reported that their business has been impacted by more than three API attacks per month while 5% said they were hit with more than six attacks per month. Viewed on an annual basis, this finding means the security team is battling between 36 and 72 API attacks every year.
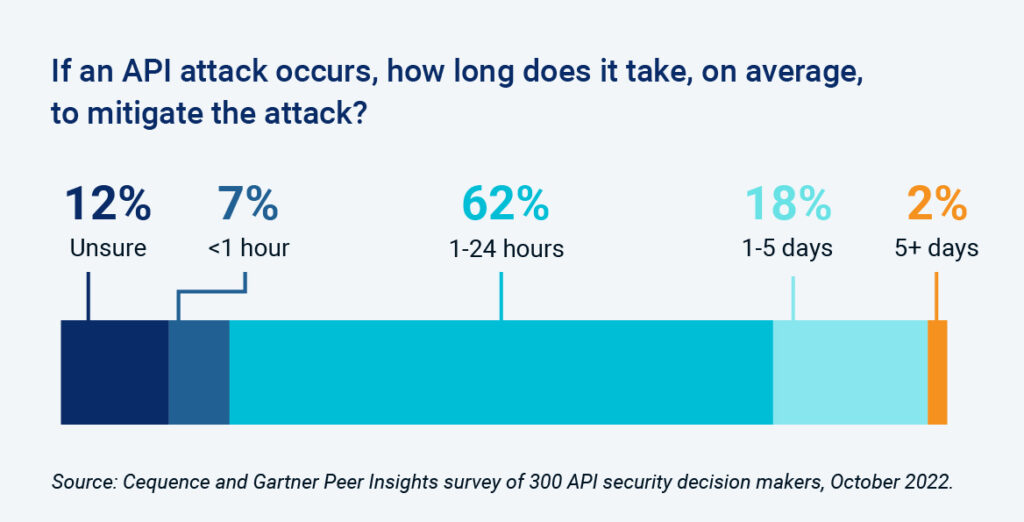
In terms of response time, 7% stated that they were able to respond to an attack in an hour or less while 62% said it took as long as 24 hours and 18% stated it takes up to 5 days. In a worst-case scenario, some of the respondents may be battling API attacks all year long (72 attacks x 5 days = 360).
The somewhat delayed response to attacks may be tied to the disparate API security infrastructure used and the types of attacks respondents were seeing. The most common tools used to protect APIs are web application firewalls (WAFs) at 71% and API gateways at 63%, neither of which is designed to protect against the most common threats observed – authentication enforcement (71%) and content inspection (63%).
Why Legacy Tools Fall Short on API Security
WAFs were originally designed to address PCI section 6.6 requirements, using signatures to detect known vulnerabilities as described in the OWASP Web Application Top 10 Threats list. API gateways are designed to help organizations aggregate and manage APIs, providing access control and basic security functions such as rate limiting and IP block lists. Both of these tools inadequate for addressing the top API security concerns expressed by survey respondents.
Another factor contributing to the delayed response is the lack of integration and alignment between tools and teams. The survey findings showed that nearly half of the respondents (49%) state that better integration between multiple API security tools would be most impactful for improving response times. The results also showed that 35% felt that better alignment between security and development teams would impact API security in a positive way.
Cequence Unified API Protection
The Cequence Unified API Protection (UAP) solution addresses the challenges with API sprawl with a broad set of technology integrations designed to ensure visibility into all APIs regardless of how and where they may be deployed. Deployed as a SaaS or as a hybrid architecture, the Cequence UAP solution provides complete coverage for every phase of your API protection lifecycle.
- Discover Public Facing API Attack Surface: API development and deployment is often distributed across many groups, introducing the risk of APIs deployed as a shadow API. The Cequence UAP solution solves that challenge by continuously assessing your public facing APIs and resources to provide an attackers view of your organization’s attack surface, including cloud hosting services, any associated API endpoints, and servers that may be vulnerable to Log4j and LoNg4j exploits.
- Centralized Inventory Tracking of Known and Unknown APIs: The Cequence UAP solution integrates with a range of infrastructure components to provide centralized API visibility and inventory tracking of all the APIs deployed within your environment, including shadow and zombie APIs.
- Strengthen Compliance and Data Governance Controls: Cequence UAP helps organizations enforce compliance and governance controls with proactive API risk analysis and remediation. Predefined and custom risk assessment rules help organizations teams find and remediate coding errors that introduce sensitive data handling and authentication vulnerabilities that can lead to data governance and compliance violations.
- Detect Sophisticated API Attacks: The Cequence UAP solution detects threats in your APIs using ML-based analysis based on a threat database with millions of records. Behavioral fingerprinting continually tracks sophisticated API attacks, even as they retool to evade detection.
- Flexible, Real time Mitigation Responses: Real-time responses to API attacks range from basic block and rate limiting to HTTP header insertion and deception, all executed in real time, per policy or per app, eliminating the time-consuming reliance on integration with third-party WAFs.
The Cequence Unified API Protection solution ensures customers can continue to reap the competitive and business advantages of ubiquitous API connectivity. The Cequence UAP results in attack futility, failure, and fatigue for even the most relentless of attackers. It significantly improves visibility and protection while reducing cost, minimizing fraud, business abuse, data losses and non-compliance.
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.




