2021 Gartner® Hype Cycle™ report is an information-packed document often used by clients as a means of gauging their investments in a particular technology segment. The 2021 Hype Cycle for Application Security is no exception, covering roughly 30 segments within the application security space. Within the report, Cequence Security was recognized by Gartner as a Sample Vendor in both the API Threat Protection and Bot Management segments.
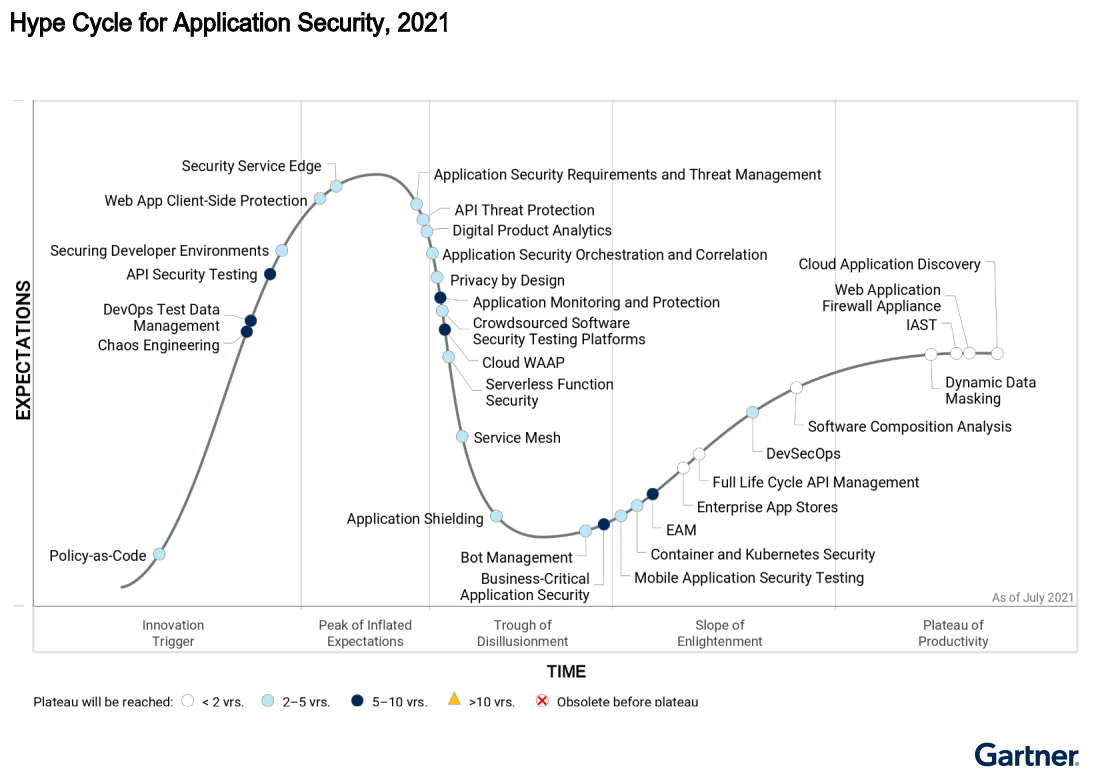
Cequence is the only vendor to be recognized in both API Threat Protection and Bot Management segments, a recognition that we believe confirms our belief that a comprehensive API security platform MUST be able to detect API threats and natively mitigate them in real-time while also analyzing your APIs to help you find and remediate vulnerability exploits caused by coding errors. Most API Security vendors just detect threats and then rely on third parties for mitigation. Cequence is the API Security leader that covers all stages of the API Security lifecycle – Discovery, Detection, and Defense, natively without relying on any third-party solutions.
Perfectly Coded APIs Can Be Attacked
APIs are the connective tissue for everything we do digitally, making the importance of protecting them from all forms of malicious use critically important. The user interface for your mobile and business app that is designed to deliver an engaging user experience is supported by APIs connecting back to compute resources located elsewhere – be it the cloud, the data center, or both. Validating that APIs are the development tool of choice, the most recent Cequence Security API Usage and Threat Report found that 14.4 billion or 70% of the 21.1 billion application requests analyzed were API-based. Confirming that even perfectly coded APIs are susceptible to a attack, the Threat research team found that 80% of the nearly 2 billion attacks mitigated were API-based. From the Bot Management Section of the Hype Cycle for Application Security:
“Bot traffic continues to rise, along with increasing sophistication of bots. Attackers leverage bots to automate their attacks onto enterprises’ online assets, including scraping, scalping, and credential stuffing. The rise of “hu-bot,” combination of specialized bots with human-operated fraud farm services, requires ever-improving sophistication in detection and response.” — Hype Cycle for Application Security, 2021, Bot Management Section, Jeremy D’Hoinne, Ramon Krikken, Akif Khan
Cequence is a pioneer in API security as we have been focused on it since 2015 when most of the vendors did not exist or were still in stealth mode. We took the approach that even the most perfectly coded account registration, shopping cart, or language translation API can be attacked and built a platform that:
- Assumed that bad actors will use both APIs (and web) endpoints to make their attacks appear legitimate, easily bypassing JavaScript and SDK-based prevention tools and other security tools (e.g., firewalls, IPS, WAFs, Security Gateways, and fraud tools).
- Uses a multi-dimensional machine learning engine called CQAI to create a Behavioral Fingerprint based on the analysis of the tools, infrastructure, credentials and behaviors used in every API transaction. The Behavioral Fingerprint casts the widest net with the highest efficacy possible and confirms malicious (or not) intent.
- Leverages NetworkIQ, the world’s largest API security database with more than a 100M IP addresses and information on more than 200,000 malicious organizations. NetworkIQ combined with Behavioral Fingerprinting helps our customers confidently prevent attacks with a high degree of efficacy.
Most importantly, the CQAI analysis can immediately be translated into real-time mitigation policies that include block, rate-limit, geo-fence and deception.
API Security with a Prevention-First Approach
Unlike some of the API security upstarts, I am of the opinion that shift left efforts are improving security for APIs and applications – but they are not replacements for the protection steps described above. Improving API security on the development side is a constantly evolving team effort – it’s not a one-and-done. Developers are human, errors are made, processes are not followed, and adjustments need to be made to make ensure these security gaps are discovered and remediated quickly. APIs discovered to be vulnerable yet too critical to be removed from production need to be protected from attacks while fixed on the backend. From the API Threat Protection Section of the Hype Cycle for Application Security:
“Because APIs are typically used for access to data or application functionality, often linked to systems of record, the impact of an API breach can be substantial. Privacy regulations typically require reporting if private data is breached through an insecure API. APIs are easily and intentionally programmable, so a vulnerability can leak large volumes of data. That it can be challenging to separate valid API use from nefarious access raises the risk of blocking valid use.” — Hype Cycle for Application Security, 2021, API Threat Protection Section, Mark O’Neill, Jeremy D’Hoinne.
The Cequence Platform builds upon our prevention-based expertise, adding a rich set of features that encourages collaboration between security and development teams – without injecting friction or additional work.
- Security teams can use the platform to identify the entire attack surface area, effectively seeing what an attacker might see. Findings can be translated into actions quickly to close potential security holes.
- Both security and development can use the Platform API discovery, inventory tracking and risk assessment to reign in the API footprint while uncovering and remediating common errors like poorly implemented authentication; exposed sensitive data; and specification non-conformance.
- Development teams can use the platform to automatically generate OpenAPI 3.1 specifications for out-of-spec APIs, resulting in improved quality, consistency, and security.
As the CMO of Cequence, I get the pleasure of seeing firsthand how our products help our customers discover the true size of their API footprint, assess and remediate risks while continuously looking for and blocking automated attacks, business logic abuse and exploits natively, and in real-time. We believe these mentions are great validation points for our customers, our prospects, and our team, in addition to the creation of a brand new cybersecurity category – API Security.
Schedule a personalized demo now.
Gartner, Hype Cycle for Application Security, 2021, 12 July 2021, By Joerg Fritsch
Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from Cequence.
GARTNER and Hype Cycle are registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and are used herein with permission. All rights reserved.
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.




