Made popular by television talk-show host David Letterman, an avid application security enthusiast and obsessive list maker, top 10 security lists have driven many organizations’ security programs, giving them a framework for a particular security initiative. In some cases, the lists have been used with tunnel vision, resulting in security gaps. While the OWASP Web Application and API Security Top 10 lists are the most common and well-known security lists, OWASP has a wide range of lists that may be applicable to your organization. Regardless of what list you may choose to use for your security initiative, these lists are ranked as top 10s because they describe the most severe threats. This means that these lists should be used as a starting point and organizations should always look beyond the top 10 lists to find the other many hundreds of threats their organization may be subject to.
Who or What is OWASP?
OWASP stands for the Open Web Application Security Project, a nonprofit foundation that works to improve the security of software. The major thrust of OWASP comes down to projects run by groups of individuals that are part of OWASP chapters worldwide. OWASP is a large, global organization of dedicated professionals who volunteer their time and talents to make software more secure. Each OWASP Top 10 list represents a project.
What is the OWASP Web Application Security Top 10?
The oldest of the OWASP Top 10 lists is the Web Application Security Top 10 and it is designed to address the 10 most critical web application security concerns. Much of this list focusses on protecting the types of applications that interact with via a web browser. The list contains protections for client side privacy and security as well as the web application platform.
If you use online banking, or have bought goods and services from an online retailer, then you have benefitted from the OWASP Top 10 effort. The Web Application Top 10 list is thought to be the initial standard for protecting security for each of these industry platforms. In an effort to improve security for credit cards, the Payment Card Industry (PCI) dictates that any application accepting or using credit cards must not have any OWASP Web Application Top 10 vulnerabilities.
What are the OWASP Top 10 vulnerabilities? As shown in the list below, they represent problems that are common within web applications that often result in a security incident or data breach. The data determining which vulnerabilities make the list and their associated order is derived from the previous three years of breach data and input from application security experts. While the list is updated every few years, make no mistake, the current 2021 list remains relevant today. Outside of improving application security testing processes and procedures to find and fix vulnerabilities before they are exposed, the OWASP Web Application Threats are commonly addressed by Web Application Firewalls.
OWASP Web Application Security Top 10
- A01:2021 Broken Access Control
- A02:2021 Cryptographic Failures
- A03:2021 Injection
- A04:2021 Insecure Design
- A05:2021 Security Misconfiguration
- A06:2021 Vulnerable and Outdated Components
- A07:2021 Identification and Authentication Failures
- A08:2021 Software and Data Integrity Failures
- A09:2021 Security Logging and Monitoring Failures
- A10:2021 Server-Side Request Forgery
What is the OWASP API Security Top Ten?
While many web applications have long used APIs as the backend, you should not assume your APIs fully covered if you focus solely on the OWASP Web Application Top 10. As previously mentioned, the original list is for web applications specifically applications that are utilized via a browser. The OWASP API Security Top 10 covers applications that use APIs to move data around or are the interface for the application data, such as a mobile application. From the folks at OWASP, “API Security focuses on strategies and solutions to understand and mitigate the unique vulnerabilities and security risks of Application Programming Interfaces (APIs).”
Many of the security incidents in the last two years have leveraged API-specific vulnerabilities that were discovered by looking at normal application flow via a reverse proxy or a similar process. These applications didn’t have web pages to go to, the APIs were embedded within consumer electronics, like in the case of a Peloton fitness bike or are a consumer application for use with mobile, like in the case of Brew Dog.
What are the API vulnerabilities within the OWASP API Security Top 10 list? The list extends beyond the web application variants to include things like authentication and authorization flaws, mismanagement of the application, problems with allowing automated attacks on the platform, etc. Organizations that are moving down an API-first methodology, but still have web applications should use both of these lists as starting points for their security and compliance initiatives.
OWASP API Security Top 10 List
- API1:2023 Broken Object Level Authorization
- API2:2023 Broken Authentication
- API3: 2023 Broken Object Property Level Authorization
- API4: 2023 Unrestricted Resource Consumption
- API5: 2023 Broken Function Level Authorization
- API6: 2023 Unrestricted Access to Sensitive Business Flows
- API7: 2023 Server Side Request Forgery
- API8: 2023 Security Misconfiguration
- API9: 2023 Improper Inventory Management
- API10: 2023 Unsafe Consumption of APIs
API10+: Extending Beyond OWASP API Security Top 10
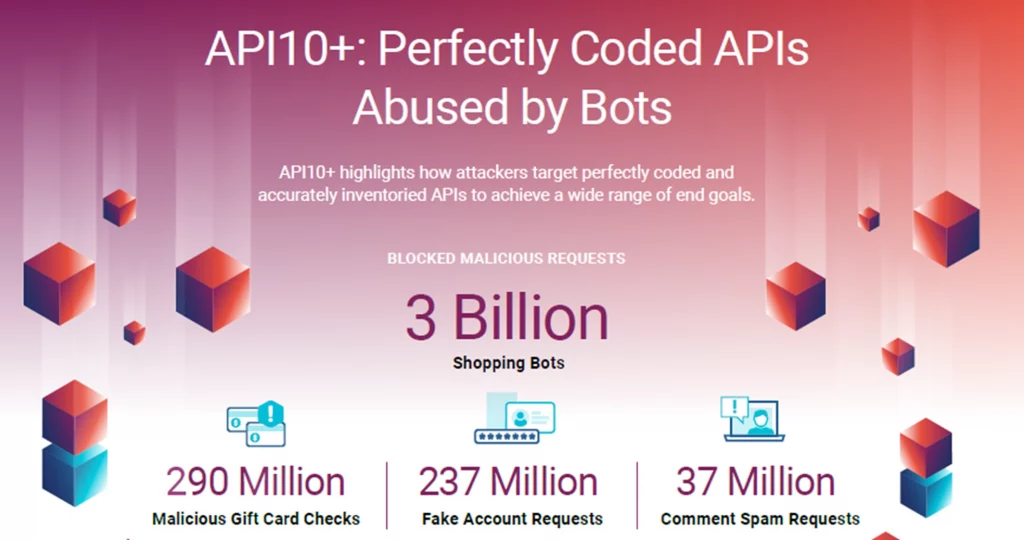
A singular focus on addressing the OWASP Top 10 lists is a good start, but complete API protection will be illusive unless you have a complete understanding of how APIs – both correctly coded and those with errors – can be attacked. This includes how a risk is discovered, the tactics, tools, and procedures attackers use to exploit it, and how attackers will react to resistance. This means not only making sure that your APIs are not susceptible to the OWASP API Security Top Ten as a starting point, but also to look at what can be defined as API10+, a category that encompasses the many different ways attackers target perfectly coded APIs that either do not cleanly fall into any of the OWASP API Security Top 10 threats or use a combination of them to achieve their goal. As documented in the API Protection Report, First Half 2022, the CQ Prime Threat Research blocked roughly 3.6 billion malicious requests, making API10+ the second largest API security threat mitigated during this timeframe.
What is the OWASP Automated Threat Handbook?
OWASP accurately states that “Web applications are subjected to unwanted automated usage – day in, day out. Often these events relate to misuse of inherent valid functionality, rather than the attempted exploitation of unmitigated vulnerabilities.” The OWASP Automated Threat Handbook (OAT), was created to help drive the adoption a common language framework for different groups (e.g., DevOps, architects, business owners, security engineers, purchasers and suppliers/vendors) across all industries to use when discussing web application threats. Organizations should use this list as a complement to the Web Application and API Security Top 10 lists.
Other OWASP Top 10 Lists to Consider
- The OWASP Mobile Top 10: Started in 2015 and revamped since then, this list is comprised of vulnerabilities in the actual mobile application as opposed to the backend application servers. As we all have mobile devices and increasingly count on the applications installed on them, this list is important. The latest revision to this list, 2024 is now available. The items on the list sound extremely scary, including items such as insecure data storage and insecure communication, so any organization focused on developing mobile-side application should use this list as an extension to the web and API-specific lists.
- The OWASP Kubernetes Top 10: The newest Top 10 for Applications is driven by the adoption of Kubernetes as application infrastructure and covers the vulnerabilities that can impact the servers as well as the applications. The Kubernetes Top 10 is about prioritizing risk in the Kubernetes ecosystem and should be considered if your organization is using Kubernetes.
- The OWASP Top 10 Proactive Controls: The question often comes up “why are developers putting vulnerabilities in their software” and the use of proactive controls steps toward solving that issue. Developers, like anyone that makes a mistake, don’t put vulnerabilities in software on purpose. Developers are just trying to get their jobs done as efficiently as they can. In order to code securely, one must understand where to apply security concepts. For instance, an authentication routine may now have a better and more secure way to handle passwords. When updating software, calling this new library might be needed in order to add this security feature. How would a developer know this is possible or that it exists? This is the job of proactive controls. Reviewing libraries for better security features as well as possibly better frameworks, is important and up towards the top of the list. As one develops the next feature set, the next enhancement, reviewing the controls allows for a step where one can ask the question “is there a more secure way to do this?”
As a longtime member of the OWASP community and a passionate application security advocate, I believe that the industry is at risk of relying too heavily on the top 10 lists. Whenever possible, I recommend that security teams who are just getting started with an application (or API) security initiative look to OWASP as a mechanism to get started. The nature of top 10 lists is that they may be a great starting point to help you address some of your risks. But remaining risks, even those not found on a list, need to be identified and addressed in order to avoid compliance violations, data loss, and business disruption.
Cequence Security and the OWASP Lists
Cequence Security believes in taking a holistic approach to defending against API-related risks with a market-defining solution that addresses every phase of the API protection lifecycle. The Cequence Security Unified API Protection platform is the only offering that protects your organization from every type of attack on the OWASP API Security Top 10, OWASP Web Application Security Top 10 and OWASP Automated Threat list.
Schedule your personalized demo today.
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.




