The FBI is warning security professionals to be on the lookout for increased use of residential proxies to execute a credential stuffing attack. The warning is a combination of good news and bad news.
The Good News: Data Shows Elevated Residential Proxy Awareness
The warning raises awareness around the use of residential proxy services by cybercriminals, specifically for credential stuffing attacks. It follows the recent news around 911 proxy service going dark and the takedown of RSOCKS proxy service by law enforcement. To improve the detection of a credential stuffing attack via residential proxies, the FBI warning makes the following security solution recommendations:
- Watch for user agent usage patterns indicative of malicious activity
- Implement security tools at the edge that go beyond CAPTCHAs
- Reinforce the message that password re-use is poor security practice
- Use fingerprinting and other analysis techniques to weed out credential stuffing attacks traversing residential proxies
The residential proxy warning includes data on how the OpenBullet attack toolkit is used to automate the use of stolen credentials for automated attacks. OpenBullet includes easy access to predefined credential stuffing attack configs that leverage residential proxies as a means of masking location and identity. One of the more popular attack tools, OpenBullet simplifies the act of launching any type of automated attack, not just credential stuffing attacks.
The Bad News: Residential Proxies More Commonly Used Than Implied
The warning lacks any data on the popularity of residential proxies and how easy they are to access. Residential proxies are also known as Bulletproof Proxies. A residential proxy is an IP address of a compromised PC, cable box, garage door opener, doorbell, or even a refrigerator. The IP addresses (Proxies) become part of a commercially available service marketed for legitimate uses like website testing. These services also provide attackers access to vast number of IP address that are used to execute large scale, automated attacks while masking identity and location. Proxy solution features include the management dashboard access with the ability to schedule attacks, route traffic through specific geographic locations and monitor traffic patterns.
A quick web search for proxy solutions provides easy access to numerous offerings, complete with payment plans and customer testimonials. The providers shown in the image below collectively claim to have more than 130M IP addresses available globally.
Noted in the warning, executing a credential stuffing attack is a common use case for residential proxies, but not the sole use case. Any automated attack (e.g., from brute force attacks to enumeration, content scraping and fake account creation) will use proxies to mask identity and location while achieving scale.
Bots-as-a-Service: A One-Stop Shop for Tools and Residential Proxies
The FBI notes how OpenBullet is used in conjunction with proxies to execute credential stuffing attacks. The warning does not include a discussion of more recent tools classified as bots-as-a-service.

OpenBullet remains popular but this new class of bots-as-a-service eliminates much of the effort required to execute an automated attack. A user can now access these services to pick from a library of bots based on their target. Once their target is chosen, a user can subscribe to the service to execute the attack. Users do not need to create scripts, find the credentials, infrastructure and tools to perform malicious automated actions. They can now access a service that combines credentials, infrastructure and tools into a one-stop-shop for them.
Protect your APIs from a Credential Stuffing Attack: API Security Best Practices Webinar
The Business Impact of a Credential Stuffing Attack
Understandably missing from the FBI report is the impact a credential stuffing attack via residential proxy enabled bots have on the business. The impact to the business can include:
- Security: Security is impacted by efforts to slow or stop the attack, often struggling to separate real from fake, or worse yet, blindsided by an unprotected, easy to access, shadow API.
- Infrastructure: Whether it’s an automated attack on a perfectly coded API, or a volumetric attack against an API coded without resource or rate limiting (OWASP API#4), the impact on infrastructure teams impacts the business. High volume attacks are known to make web sites and mobile apps non-responsive, resulting in user frustration.
- Fraud teams: Time spent investigating individual accounts, issuing account reset or delete recommendations during fake account or ATO attacks. All of which consumes time that the fraud team could spend on broader team goals.
- Marketing, Sales, eCommerce: These groups may be presented with inflated web statistics which result in poor or misleading sales program decisions, missed revenue projections and damaged vendor relationships. In an extreme case, bot-inflated statistics appear to have had a material impact on the acquisition of Twitter by Elon Musk.
- Customer Satisfaction, PR, Brand: Research shows that 57% of consumers spend more on brands to which they are loyal. Data shows that high customer loyalty generates 12%-18% incremental revenue growth per year. The high potential return encourages organizations to focus on customer retention. A bad user experience due drives customer elsewhere, resulting in a 5x increase in costs of acquiring a new customer.
A 2021 Forrester survey of 400+ organizations validates the business impact with 15% of the respondents noting bot-related losses as high as 10%.
FBI Recommendations for Blocking Residential Proxies Fall Short
The FBI security solution recommendations for stopping a credential stuffing attack and other types of cybercrime via residential proxies are too simplified and are easily evaded by attackers. The credential stuffing attack protection recommendations also increase the risk of adding friction to the end user experience. For example, OpenBullet has predefined evasion techniques for JavaScript-based security measures provided by CDN-based solutions. It has similar features to solve CAPTCHAs and to get around user agent string analysis by mimicking a range of up-to-date browsers.
Also missing from the FBI security bulletin is the discussion of APIs and how they are now used as the vector of choice for credential stuffing and other automated attacks. Data shows that threat actors love APIs because it simplifies the execution of high-volume attacks while negating the traditional agent-based security mechanisms. It is impossible to install an agent in an API like you can with a web or mobile app.
How Cequence Tracks and Blocks Residential Proxies
Residential proxy services are a critical tool for attackers who need access to easily scalable infrastructure while maintaining anonymity and masking location. The good news is that many of the proxy services are known by their IP address and organization, making them trackable over time. By using data to identify and track these services, policies can be implemented to automatically block them.
Network IQ and IP Threat Score
Boasting the largest data collection of residential proxy services, Cequence Network IQ is part of CQAI, a patented ML-based analytics engine that drives the Cequence UAP solution. A subsystem within Network IQ called IP Threat Score parses threat data to identify proxy IPs the moment they hit CQAI. The residential proxies are identified, tagged and delivered to customers in the form of both predefined policies and the dataset itself.
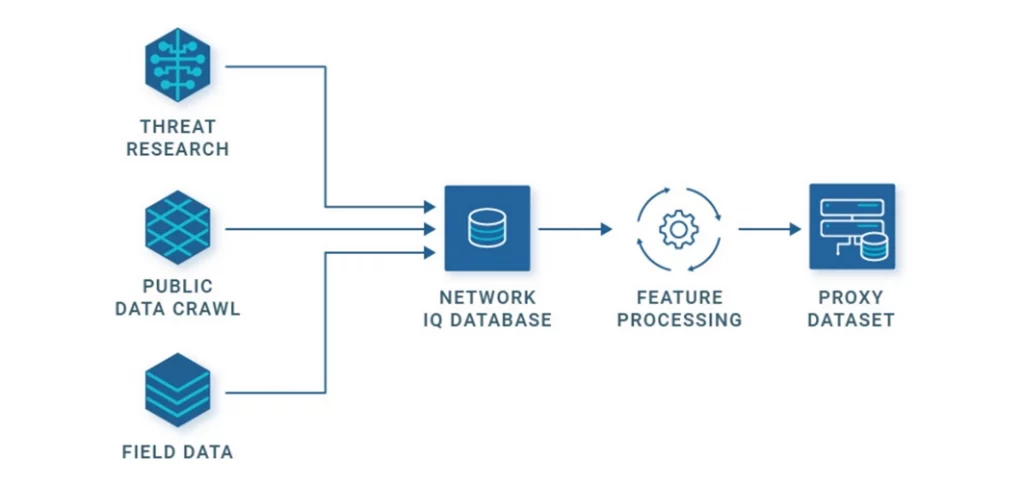
The IP data sources include:
- Passive Threat Research: Web-based crawlers continuously search public data feeds that contain information on residential proxies and IP reputation. The search results are automatically added to the Network IQ database.
- Active Threat Research: The CQ Prime Threat Research team subscribes to residential proxy providers themselves, collecting the IPs in use and adding them to the database.
- Field Data: An essential data source of malicious infrastructure, proxy IPs used in attacks are automatically tagged and added to the database.
Network IQ data collection is highly automated which allows it to adapt to the ever-changing threat landscape. Network IQ data identifies not only individual IPs, but also entire network blocks, organizations, or ASNs. The data is classified by Network IQ into datacenter and residential proxy groupings.
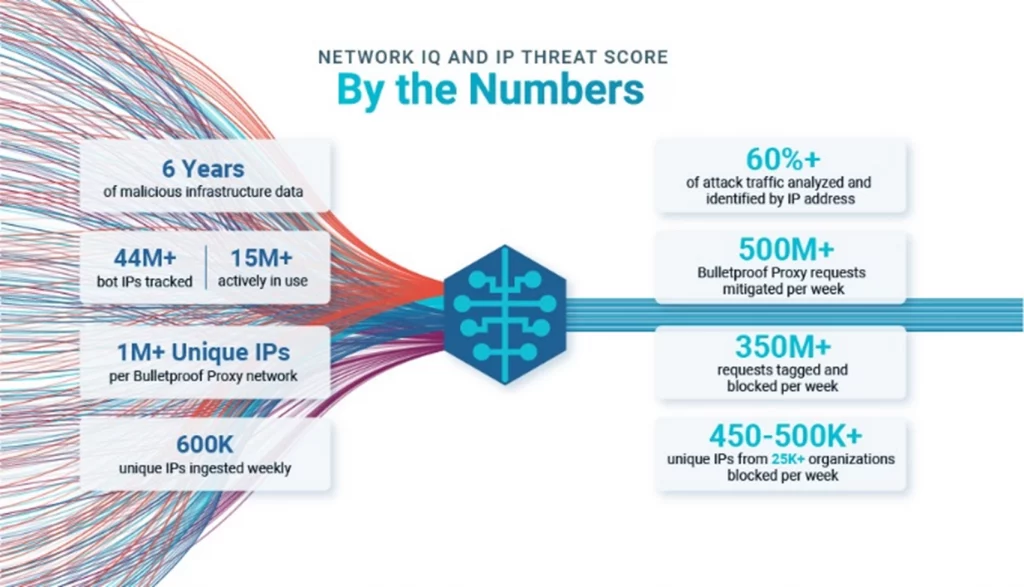
The rich Network IQ data used by IP Threat Score identifies unknown IP addresses used in automated attacks as malicious 98-100% of the time. Predefined policies using IP Threat Score can be enabled to immediately block automated attacks using residential proxies.
Schedule a personalized demo to learn how Cequence API Spartan can detect and prevent automated attacks that use stolen credentials and residential proxies.
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.




