When a hot product hits the market, it’s not uncommon to see multiple vendors follow the first market mover, selling the same or a very similar product. The 2019 research done by Brian Krebs and the CQ Prime Bulletproof Proxies research report both noted a few vendors who were marketing residential proxies (IP addresses) to the public.
As the volume of stolen credentials continues to climb with weekly breaches, new vendors are emerging to market their network of residential proxies, since this type of criminal infrastructure is popular with bad actors who use it to launch automated attacks. Today it’s easy to find multiple Bulletproof Proxy vendors marketing their residential proxies to the public.
Common Bulletproof Proxy Uses
The first legitimate proxy use case can be a pure desire from a user to avoid geolocation-based censorship of internet content. People seeking to maintain anonymity browsing the web have every right to do so, and, more importantly, a proxy can be a tool to provide whistleblowers and suppressed individuals a means to communicate anonymously. Though, it should be noted that an individual only needs a single proxy to maintain anonymity, not the millions that Bulletproof Proxy vendors advertise.
Another potentially valid use case is an organization using a proxy vendor to test new features that may appear different to users in different countries or with different types of IP addresses (e.g., residential vs. mobile). In this case, the organization can potentially take advantage of the high number of proxies offered to simulate large user populations.
While the above use cases are seemingly legitimate, unfortunately, one of the more common uses is bad actors who want to execute a cyberattack while masking their identity and location. Account takeovers, fake account creation, scraping, and API abuse are all types of automated attacks that frequently take advantage of the anonymity benefits offered by Bulletproof Proxies. To better understand the attack infrastructure our customers face, the CQ Prime Threat Research team compared the ‘base product’ of one of the new vendors to that of the older vendor used in our 2019 report.
No Honor Among Thieves
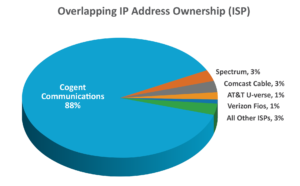 Comparing two Bulletproof Proxy vendor offerings showed that roughly 34% of 22,000 North American IP addresses were for sale from both vendors.
Comparing two Bulletproof Proxy vendor offerings showed that roughly 34% of 22,000 North American IP addresses were for sale from both vendors.
Essentially, they are both selling the same product. Both vendors offered country, state, and, in some cases, city breakdowns, allowing customers to choose the geography from which the traffic would originate. When the CQ Prime Threat Research Team drilled down into the source ISP for the overlapping IP addresses, they discovered that Cogent Communications owned 88 % (possibly a carryover from their purchase of PSI Net assets). The other 12% were distributed across the remaining ISPs.
100% Malicious Usage
Analyzing customer attack data showed that 100% of the overlapping IP addresses were generating account takeover traffic in both retail and financial services environments. Additional historical analysis of the overlapping IP addresses in those same customer environments showed they did not generate any legitimate traffic. Ever.
Retail Analysis
In retail environments, the attack traffic across the overlapping IP addresses heavily targeted web applications, with the bulk of the attack traffic originating from Cogent Communications. Interestingly, the mobile API attack traffic was more evenly distributed across several ISPs with Verizon Fios most heavily used.
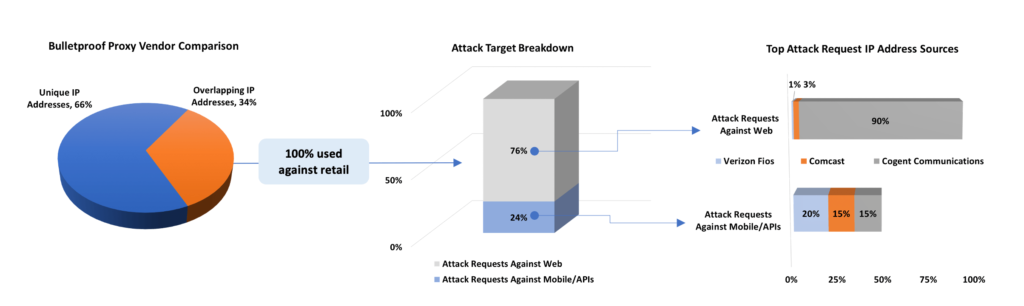
Image 2: Overlapping IP address analysis for retail customers
Financial Services Analysis
Applying the same analysis to financial services customer data, the targets and the ISPs most commonly used were flipped. The mobile APIs were targeted almost exclusively, with 88% of the attack traffic originating from IP addresses owned by Cogent Communications. Whereas the retail analysis showed attack traffic against web applications more evenly distributed across several ISPs, the financial services data shows 88% of the web attack originating from Cogent Communications.
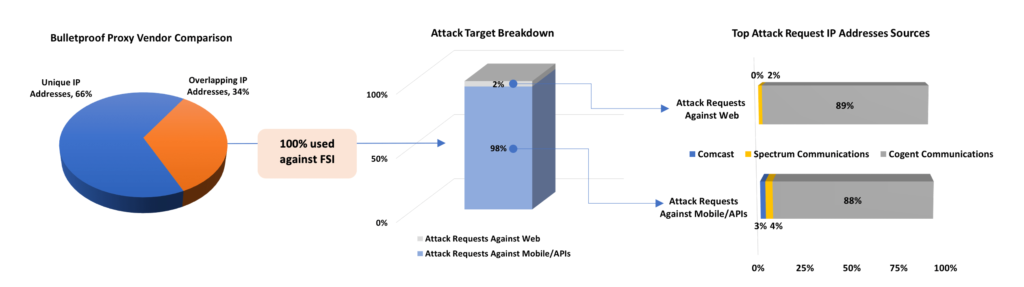
Image 3: Overlapping IP address analysis for financial services customers
Building a Case for Outright Blocking
In most customer environments, there is a reluctance to blacklist large blocks of residential IP addresses because there is always a possibility of blocking a legitimate user, resulting in a false positive and an unhappy customer.
In reality, what are the chances of a false positive occurring? When the data shows that the IP address is known to generate ONLY malicious traffic and has never generated any legitimate traffic, as mentioned earlier, the case for blocking becomes more powerful, and the chance of a false positive is low.
In cases where the probability is relatively high, for example, a retailer and a customer, both in the U.S., we observed less than 0.8% of the overlapping IPs EVER appearing in good traffic over a four-month period that included the peak periods of Thanksgiving, Black Friday & Christmas. The highest potential false positive rate observed was a maximum of 4% of all the overlapping IP addresses EVER generating legitimate traffic over an entire year (2019). The traffic from these IPs represented a minuscule < 0.1% of all traffic from known Bulletproof Proxy vendor IPs.
While some of these false-positive rates are still too high to be acceptable over a long period, we’ve found that during bot attacks, these IPs seldom generate any legitimate traffic. This is where learned models that can detect and block these Bulletproof Proxy IPs while they are committing abuse become important, and then automatically allow them to “become good again.”
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.