Today, bad actors are increasingly exploiting API security gaps, allowing them to exfiltrate data, commit fraud or take other actions that can come back to haunt your organization. With the spooky season upon us, I wanted to cover some of the more chilling real-world API attack scenarios I’ve spotted in both Cequence customer environments and my research.
13 Scary Security Gaps
#1 Threats Lurking in Shadow APIs
![]() In a recent survey, we found that only 16% of teams had an automated tool that inventoried APIs.
In a recent survey, we found that only 16% of teams had an automated tool that inventoried APIs.
With API use exploding, many organizations are, at minimum, aware of APIs within their own applications. However, misconfigurations during fast-paced development cycles and numerous third-party integrations introduce new risks left and right — leading to unknown and unmonitored API endpoints.
#2 Zombie APIs — Be Very Afraid
Remember rule #2 in Zombieland?
(It involves ensuring no 🧟 will be coming back to bite you.)
The same goes for APIs. Ensure old, insecure versions of your APIs are really put to rest (or at least closely monitored). You may have left them accessible for a specific reason. For example, maybe some of your customers had old devices that couldn’t take updates. However, you should undertake any decision to keep older, under-secured API versions accessible with careful consideration and the complete understanding it could result in a breach.
#3 Unlocked Doors
Unauthenticated APIs can lead to some chilling scenarios. This is especially true for public-facing APIs that handle essential business information or contain data subject to regulatory compliance standards like PCI-DSS or PHI.
One common reason cited for failing to implement authentication is that the API was intentionally left open in the past to accommodate a legacy application’s limitations. However, by leaving the door unguarded indefinitely, attackers are more than happy to slip in uninvited too.
#4 Even Scarier: Authenticated but Not Authorized APIs
Suppose your backend is not enforcing strong authorization.
In this all-too-common API risk, authenticated users can exfiltrate information available to other users by simply enumerating identifiers. In that case, any user logging in will be able to poke around and grab information over the same API by simply changing their user identifier.
#5 Proliferating API Authentication Options
It’s common for development teams to support multiple authentication approaches for different consumers of their APIs. However, while convenient for users, this results in a fragmented authentication approach for the API that becomes hard to manage for application owners throughout an API’s lifecycle.
A potential weakness in any of those approaches, like those mentioned above, can compromise security.
#6 Bad Actors Masquerading as Legitimate Users
Today’s bots are excellent mimics. They can blend in with regular user traffic, make use of vetted (stolen) credentials, switch up their IPs, and make perfect requests — getting away with activities like gift cards and reward point fraud.
It can be hard to spot them lurking among your legitimate human also using APIs.
#7 Unmasked PII Pain Points
Are your APIs whispering secrets?
Sometimes published APIs expose more data than necessary when relying on clients, not back-end systems, to filter the data. Verbose error messages are an excellent example of this. They can tip-off attackers, allowing them to compile a list of good vs. bad inputs, steal data, or gather intel for a more significant attack.
#8 Screaming, Howling APIs
If API call and resource consumption limits aren’t clearly defined, you could be facing a screeching mess. Attackers can create a wall of noise, overwhelming your backend with denial-of-service attacks by submitting API request after API request.
A variation of a denial-of-service attack, this threat can take out critical services bringing areas of a business to a standstill.
#9 Signs of Paranormal Activity
Unusual activity in your environment and against your APIs may not lead you to call the Ghostbusters this Halloween, but it may indicate the need for improved bot detection and mitigation.
Our threat research team has a four-pillar detection methodology you can learn more about, but common red flags include:
- Activity on outdated or older endpoints
- Spikes in failed logins and password resets
- Signs of known bad infrastructure, such as bulletproof proxies
- Unusual account creation patterns
#10 Business Logic Abuse
Savvy attackers are always looking to exploit your APIs, using them “as designed” but achieving unattended and malicious outcomes. One example I’ve encountered includes bad actors decompiling a mobile application to discover the account login APIs, and they went on to execute an automated attack. If an attempt was successful, the bad actors then tried to commit financial fraud by transferring funds across the Open Funds Transfer (OFX) API.
#11 Frightful Exposures
While third-party APIs and public repositories can be undeniably useful, they can also lead to a severe jump scare if you don’t take proper precautions. ‘Set it and forget it’ safelisting can leave organizations exposed. Additionally, detailed API spec frameworks that are readily available on repositories like GitHub can help attackers plan and pull off a perfect heist for your crown jewels.
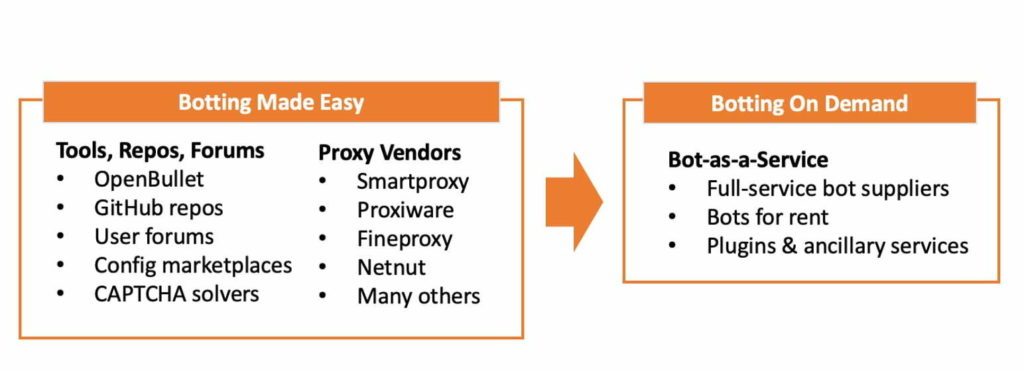
#12 Trick-or-Treating Botters
The general availability of Bots-as-a-Service has made it easy for bad actors to get access to ‘treats’ using your APIs as a part of their attack strategy.
#13 No Cequence Security!
Cequence Security helps you spot API Security gaps and trickster botters so that you can protect your business and data. Our machine-learning technology helps organizations avoid the threats and risks listed above — without introducing friction to end-users or modern development processes.
|
API Discovery and Risk Assessment
|
Automated Threat Prevention
|
Fraud Prevention
|
Avoiding an API Horror Scenario
As threats, including bot attacks, continue to evolve, APIs remain a popular target. While security best practices are maturing, the fast pace of development and the increasing sophistication of attackers can leave many organizations with security gaps.
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.




