Cequence has partnered with AWS to combine Cequence API Security and Bot Management products with AWS Web Application Firewall (WAF) and AWS Shield to offer a best-of-breed cloud WAAP. Increasingly, our customers have asked if we could provide WAF and DDoS capabilities in addition to our API security and bot management offerings, so we worked with our longtime partner, AWS, to deliver an enterprise-class cloud WAAP capable of scaling to the largest enterprises.
What is WAAP?
Web Application and API Protection (WAAP) is a term coined by Gartner that encompasses products that protect web applications and APIs from attacks and includes API security, bot management, WAF, and DDoS protection. Originally most WAAP solutions were on-premises or hybrid, more recently full cloud WAAP deployments have become more common.
The AI-Enabled World Needs WAAP
AI is changing the game when it comes to enterprise security. Whether it’s protecting the business from unwanted scraping by AI bots, blocking AI-enhanced attacks, or ensuring sensitive data isn’t exfiltrated, new threats are targeting applications and APIs. Cequence WAAP protects applications and APIs against malicious AI out of the box, ensuring Cequence customers are protected throughout the rapidly changing landscape.
Why Cequence WAAP?
Cequence WAAP brings AWS WAF results into the Cequence Unified API Protection platform dashboard, enabling users to see what rules were triggered by malicious activity.
In Gartner’s April 2025 Market Guide for Cloud WAAP, they included three recommendations for enterprises in the market for WAAP. We believe it’s clear that Cequence WAAP is ideally suited to address each one.
- If API Security is important to you, consider WAAPs that can discover APIs, generate API specs, detect API threats, and mitigate attacks. Cequence WAAP automatically generates API specs, detects API threats whether they are coding errors or business logic attacks on perfect-coded APIs, and has built-in mitigation options including blocking, rate limiting, header injection, and deceptive responses.
- Bot attacks are becoming more sophisticated. Consider switching to WAAPs that use AI/ML to reduce alert fatigue, perform behavioral analysis, and identify sophisticated threats/attacks. Explore advanced capabilities that can detect bots that can bypass CAPTCHAs. Cequence WAAP protects against even highly sophisticated attacks, whether low-and-slow or high volume. Our network-based approach leverages ML to analyze behavioral intent and requires no application modification such as JavaScript CAPTCHAs or SDKs.
- Organizations subject to data localization should consider WAAPs that have deployment flexibility in datacenter/region of preference. Cequence WAAP can be deployed in regions around the world, conveniently co-located near the customer’s applications to reduce latency and avoid application performance degradation.
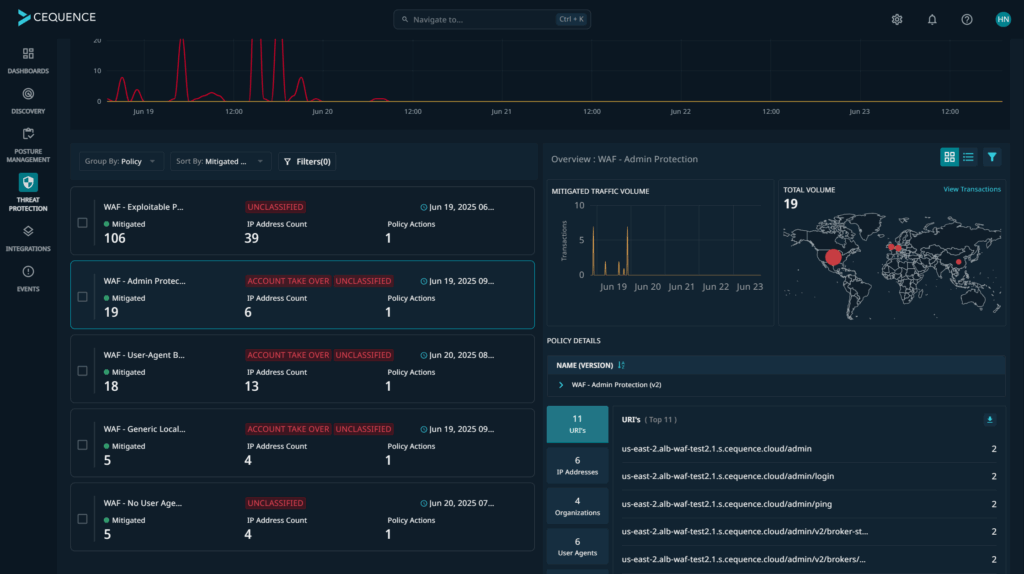
Triggered AWS WAF rules are viewable in the Cequence UAP dashboard.
Cequence WAAP Components
Cequence WAAP combines Cequence API security and bot management products with AWS WAF and AWS Shield.
API Security
A core module of the Cequence Unified API Protection platform (UAP), Cequence API Security offers API discovery, security posture management, testing, and remediation.
- Comprehensive API discovery and inventory
- Automatic API spec generation
- Continuous, real-time risk visibility
- Sensitive data exposure prevention
- Integrated API security testing
Bot Management
Also a core module of UAP, Cequence Bot Management provides advanced bot detection, mitigation, and fraud prevention requiring no application modification.
- No application modification required
- Industry-leading bot detection
- Real-time mitigation
- Rapid time to value
- Fraud prevention
Web Application Firewall
AWS WAF is a powerful, high-performance WAF with a comprehensive set of rules and policies to protect against common web application attacks.
- OWASP Web Application Top 10 protection: Comprehensive protection against common web application threats and vulnerabilities
- Protection for admin interfaces: Prevents unauthorized access to administrative interfaces to prevent compromises and data breaches
- Protection from malicious input patterns: Protects against Log4j exploits, Java deserialization attacks, localhost bypass attempts, and other known malicious patterns
- SQL injection attack prevention: SQL and extended pattern matching blocks sophisticated database exploitation attempts
DDoS Protection
AWS Shield protects against large-scale DDoS attacks that can overwhelm the operation of your APIs and business, provides comprehensive coverage across the globe, and provides 99.99% availability against common infrastructure attacks.
- Layer 3/4/7 protection: Protects against SYN floods, UDP floods, and reflection attacks with always-on network flow monitoring
- Comprehensive coverage across all AWS regions and edge locations with automatic detection and inline mitigation capabilities
- Provides automatic DDoS protection at 99.99% availability against common infrastructure attacks
Benefits of Cequence WAAP
Operational Efficiency
Cequence WAAP provides a single application protection dashboard for WAF, bot management, and API security, minimizing admin complexity and overhead.
Reduced Latency
Cequence WAAP is deployed in a single cloud, eliminating multiple cloud hops and reducing latency for optimal performance.
Reduced Risk
Integrated components within a single cloud tenant also eliminates coverage gaps caused by inconsistent traffic routing.
Cequence WAAP Deployment
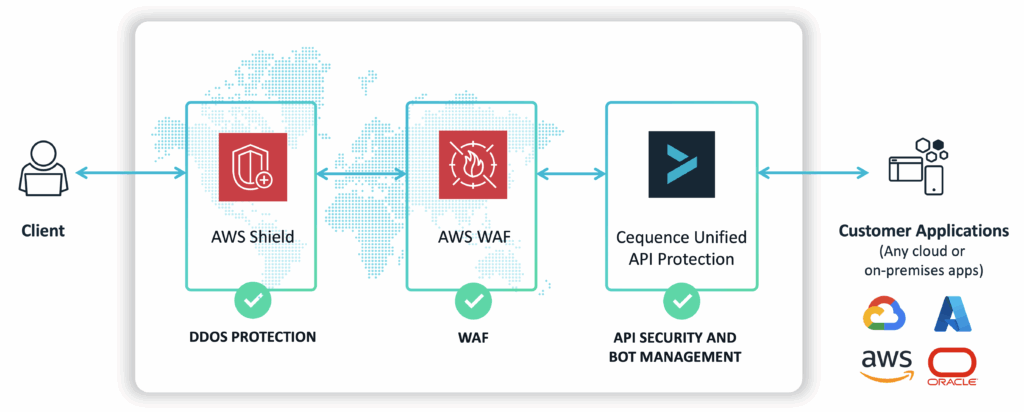
Cequence WAAP can be deployed in a single SaaS tenant, or, if the customer prefers, AWS WAF and Shield can be deployed in the customer’s tenant and Cequence UAP in a separate Cequence tenant.
Cequence also offers a Managed WAAP with all components fully managed by Cequence.
Contact us for a personalized demo.