The August 2025 Salesloft Drift breach impacted over 700 organizations when threat actor UNC6395 used compromised OAuth tokens to systematically exfiltrate data from Salesforce instances. The attackers leveraged legitimate authentication credentials, stolen from the Salesloft AI Chatbot to masquerade as trusted integrations, bypassing traditional security controls entirely.
The IP Infrastructure Pattern
Analysis of published IOCs (Indicator of Compromise) reveals the threat actor’s deliberate infrastructure choices: use of Tor exit nodes and anonymizing networks. Salesloft published a list of IOCs here. This infrastructure pattern creates detection and mitigation opportunities for defenders who understand how to leverage threat intelligence effectively.
Is IP Reputation still valuable in the Agentic AI Age?
When managing partner integrations, traditional security models often focus on allowlisting known-good IP ranges for legitimate integrations. Salesloft does publish their IP ranges that effectively should be allowlisted, and many organizations implement static IP allowlists as a first line of defense. However, this approach has fundamental limitations in the face of modern supply chain attacks.
When OAuth tokens are compromised, as in the Salesloft case, the attack traffic doesn’t originate from the legitimate service provider’s infrastructure. Instead, it comes from the attacker’s chosen infrastructure – often anonymizing networks, bulletproof hosting providers, and compromised residential networks.
Runtime IP reputation monitoring provides a critical security control that can detect when authentication tokens are being abused from anomalous sources, even when those tokens are technically valid and haven’t been revoked yet.
A Comprehensive Approach to IP Reputation
Effective IP reputation monitoring for authentication tokens should account for three different types of possibilities, each representing different levels of difficulty to implement:
1. Known Malicious Infrastructure and/or Cloud Providers
The foundation of any IP reputation system must identify established threat indicators including known suspicious hosting providers, Tor exit nodes, and previously identified attack infrastructure. In the Salesloft case, the extensive use of Tor exit nodes would have immediately flagged the malicious OAuth token usage as suspicious. This is the easiest type of reputation monitoring to implement.
Cequence Threat Intelligence Example:
The Cequence threat intelligence cloud shows that nearly all 20 IPs published by Salesloft have positive threat data, many including known, easy-to-track third-party sources.
2. Fresh Proxy Detection
Perhaps more challenging to detect are IP addresses that have recently transitioned from benign to malicious usage. These “fresh” proxies or newly compromised nodes represent a significant blind spot for traditional reputation systems that rely solely on historical bad actor data.
Residential proxy networks in particular pose a unique challenge. An IP address may have a completely clean history but suddenly become part of a botnet or proxy service. Advanced threat actors often invest in fresh infrastructure specifically to evade detection by traditional reputation systems.
Cequence Threat Intelligence Example:
The Cequence threat intelligence cloud highlights the history of a particular IP – 154.41.95.2 – which appears to have been recently announced and became a source of attack traffic, first observed as malicious this summer and continuing to be observed today.
3. Dormant Infrastructure Reactivation
The third critical pattern involves IP addresses that may have “gone dormant” in their threat activity but have recently become active again. This pattern is particularly common with infrastructure that gets periodically reused by threat actors or recycled through different campaigns.
These IPs may have been flagged for malicious activity months or even years ago, went quiet, and then suddenly reappeared in new campaigns. Traditional reputation systems often age out older threat intelligence, potentially missing these reactivation events.
Cequence Threat Intelligence Example:
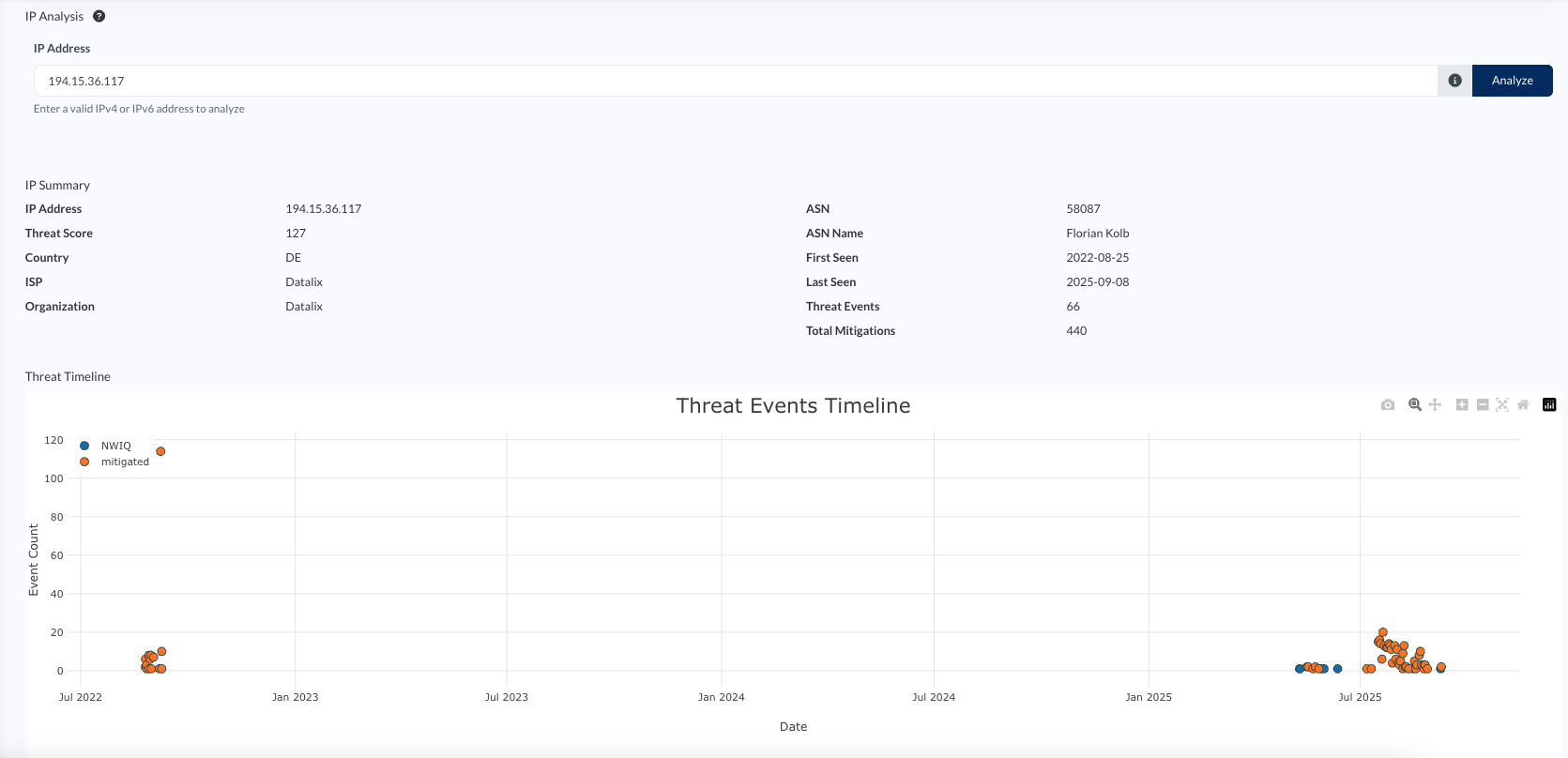
This example from the Cequence threat intelligence cloud shows two different types of dormant infrastructure. The first – 192.42.116.20 – highlights an IP address with large surge of malicious traffic over 5 years, peaking in 2022-2023, going dormant for a time in 2024, until popping back up recently this summer. The second example shows an IP – 194.15.36.117 – which was literally silent from 2022 until just this summer. Systems must be flexible enough to catch both kinds of suspicious reputation.
Implementing Token-Based IP Reputation Monitoring
Examples from Industry: One of the most straightforward examples that consumers regularly interact with in practice is in the banking industry. Users have now become accustomed to using 2nd factor authentication when they login or interact from a new IP address, or a new device. This logic extends beyond just a human logging into an application but also applies to AI-driven interactions over APIs using authentication tokens.
For cybersecurity practitioners looking to implement similar protections, several technical approaches can provide immediate value:
Real-Time Authentication Monitoring: Implement systems that can correlate authentication events with source IP reputation in near-real-time. When valid tokens are used from suspicious infrastructure, alerts should be generated immediately.
Behavioral Baseline Establishment: Establish normal geographic and network patterns for your OAuth integrations. When the Salesloft Drift integration suddenly starts making API calls from Tor exit nodes instead of known Salesloft infrastructure, this should trigger immediate investigation.
Multi-Factor IP Analysis: Don’t rely solely on binary “good/bad” IP classifications. Consider factors like:
- Hosting provider reputation and abuse history
- Geolocation anomalies relative to the claimed service provider
- Network classification (residential, hosting, anonymizing, etc.)
- Recent changes in IP ownership or classification
Integration-Specific Allowlisting: While dynamic IP ranges present challenges, maintain integration-specific allowlists where possible. When third-party services publish their legitimate IP ranges, monitor for OAuth token usage outside those ranges.
The Broader Strategic Implications
The Salesloft incident represents a broader shift in threat actor tactics toward exploiting trust relationships, which is particularly sensitive and fast-changing in the world of AI. This wasn’t a one-off compromise; hundreds of Salesforce tenants of specific organizations of interest were targeted using stolen OAuth tokens.
Organizations must evolve their security models to account for this reality. Traditional perimeter-based security models that assume valid credentials equal legitimate access are increasingly inadequate and dangerous. Instead, security teams need continuous monitoring and behavioral analysis that can detect when legitimate credentials are being abused.
The value of comprehensive threat intelligence databases becomes apparent in incidents like these. Cequence’s decade of threat data from live enterprise attacks provides critical context that distinguishes between legitimate service provider traffic and sophisticated attacks using compromised credentials.
To learn more and discuss your security needs, contact us.