Today, I wanted to delve more deeply into a comparison of API security and Unified API Protection to make the differences crystal clear. My previous blog discussed the definition of what Unified API Protection means and why organizations should adopt it over the more traditional API security offerings.
The distinction is important, given that APIs have become a development tool of choice in reaction to application componentization, competitive business dynamics and user expectations for seamless app experiences. APIs have delivered velocity and competitive advantage to companies of all sizes with IDC research calculating that up to 50% of enterprise revenue is derived from APIs. The flip side of course is it that the highly visible and well-defined nature of APIs have made them an irresistible target for attackers. As more organizations realize and acknowledge the size of their API (revenue) footprint, it’s become clear that new methods are needed to make those APIs secure.
What is API Security?
Many companies will define their offering as addressing the need for API security, which is part of the problem. API security is a broad and vaguely defined group of solutions that will mean different things to different people. As shown in the recently published ESG eBook, Trends in Modern Application Protection, API security can be defined as improving API coding quality through API specific testing tools. It can be defined as more traditional whack-a-mole type blocking, or as simply as discovery and tracking. The lack of consistency may be one of the reasons why more than 50% of the respondents felt that their API security tools were ineffective.
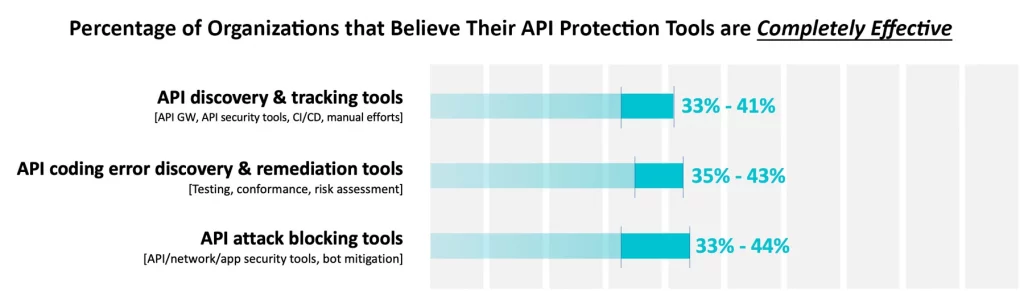
One of the possible reasons that respondents felt their tools were ineffective is the lack of completeness in the offering. An API is different than a traditional web application. Designed for machine to machine interaction and stateless in nature, APIs include the command, payload and content. Applying security only in the development stage, places an undue burden on the dev team, and does not address the fact that a perfectly coded API is still susceptible to an attack. Applying security at the time of publication without consideration for the risk profile, or possible coding errors is an invitation to introduce coding errors that can be leveraged by attackers. A more complete, end-to-end approach is required.
Introducing the API Protection Lifecycle
The API protection lifecycle takes into account each of the steps an API will traverse from inception to production, protecting all APIs, across all API implementations, channels, and infrastructure environments, and all user groups and business use cases. The API protection lifecycle should incorporate discovery, inventory, compliance, detection, prevention and testing, as shown in the image below.
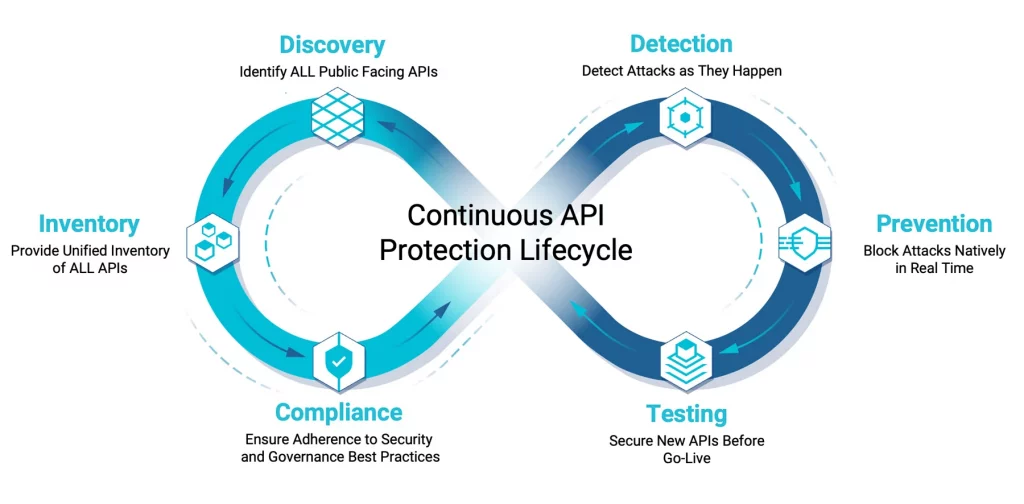
It should be viewed as a continuum because each organization will fall into a different phase that is dictated by its API maturity. When viewed from this perspective, the API protection lifecycle is a methodology designed to account for multiple types of risk, and more importantly, to provide a path to resolution.
Cequence Unified API Protection Solution
Analyzing the various API security offerings outlined in the ESG image above makes their lack of effectiveness crystal clear. As shown in the table below, each offering addresses a few of the phases of the API protection lifecycle, with none of them providing an end-to-end solution. That is until now.
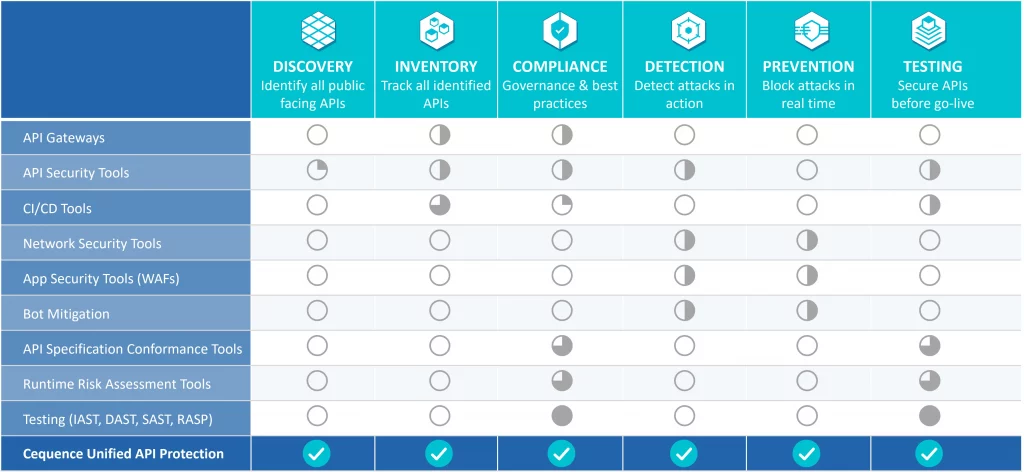
The Cequence Unified API Protection solution is the only offering that addresses all phases of the API protection lifecycle to defend your APIs from attackers and eliminate unknown and unmitigated API security risks that can lead to data loss, fraud, and business disruption. The Unified API Protection solution is comprised of:
- API Spyder: An API attack surface discovery and management tool that continuously assesses your public facing APIs and resources to show you exactly what an attacker sees from an outside-in perspective. API Spyder discovers your sub-domains, the cloud hosting service in use, any associated API endpoints, and the servers that may be exploitable using vulnerabilities such as Log4j. Results are visualized in an easy-to-use dashboard for easy and rapid remediation.
- API Sentinel: Provides an inside-out view of your APIs by integrating with any network infrastructure element to create an up-to-the-minute catalog of all your APIs, managed, unmanaged. Predefined ML-based risk assessment rules help uncover sensitive data handling, weak or missing authentication, and specification conformance coding errors for remediation.
- API Spartan: Detects and prevents the most sophisticated automated API attacks and business logic abuse using hundreds of ML rules that leverage an API threat database with billions of malicious behaviors, IP addresses and organizations. Native, policy-based response options ensure that any detected attack is blocked, in real-time, without reliance on a third-party WAF or other security component.
Security teams deploying the Cequence Unified API Protection solution eliminate unknown, unprotected, and unmitigated API risk. They achieve continuous protection of their complete API risk surface, enabling their organizations to reap the competitive and business advantages of ubiquitous API connectivity securely and compliantly. Ready to put Cequence Unified API Protection to the test? Request a personalized demo and FREE API security assessment now.
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.