Next week we will be at FS-ISAC in Washington DC (booth #60) to present (Monday, Nov. 18, 4:15PM-5:00PM) and talk with financial services organizations about how we can help them prevent fraud and theft that may result from automated account takeover attacks against their mobile and API-based applications.
It’s no secret that financial services organizations represent the crown jewels for automated account takeover attacks. More often than not, bad actors will execute their ATO attacks via the mobile application. The mobile application is decompiled and analyzed to discover how it works and how the APIs are used.
As highlighted in this video by Alissa Knight from Aite Group, the mobile APIs that enable the financial services application are used by bad actors to automate their account take overs. The Aite Group report found that 27% of FSI applications hard-code the API keys and private certificates in the apps or store them in files on the file system, thereby simplifying the execution of an automated attack.
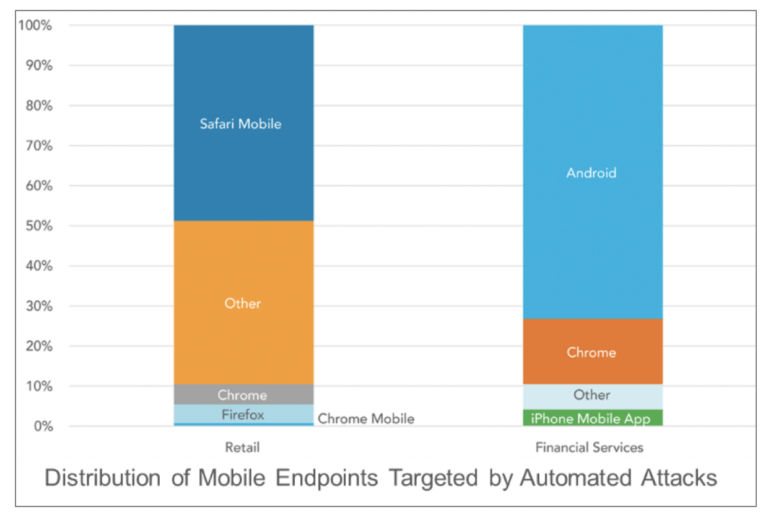
This data point is supported by data published in the CQ Prime Bulletproof Proxies research report which showed that more than 70% of the automated attacks across financial services customers targeted the mobile application. APIs are an invaluable tool for application developers who are tasked with doing more with less. Driven by mobile device ubiquity and the move towards modular applications, APIs have become the foundational elements of the application business logic. By targeting the API instead of scripting a form fill, a bad actor can leverage the same benefits of ease of use, efficiency and flexibility that APIs bring to the development community.
This data point is proven accurate by this financial services example. A financial services customer was able to detect and block an account takeover attack that targeted the mobile application account login and if successful, would transfer funds to their own (fake) account using the OFX API – the financial services funds transfer protocol.
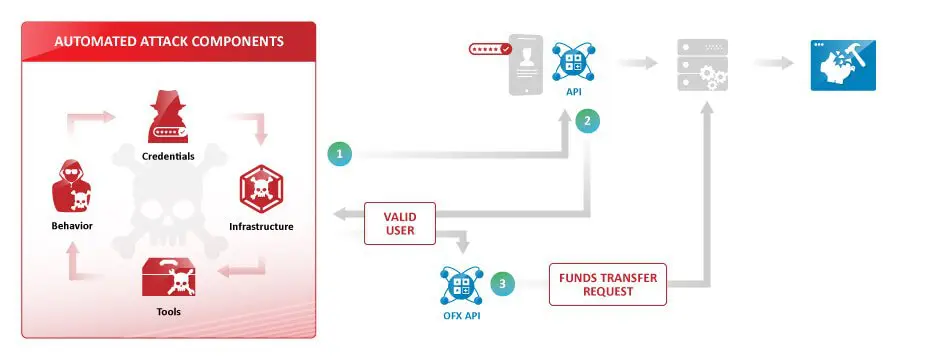
Bad actors decompiled the mobile application to (1) discover the account login APIs. An automated attack was then executed against the login API (2) and if successful the bad actors attempted to commit financial fraud by transferring funds (3) across the Open Funds Transfer (OFX) API.
Cequence was able to detect and block this ATO attack using our intelligence-based approach that automatically discovers all application endpoints – API-based, web, mobile. That visibility can then be used to protect the applications from automated attacks. The customer chose Cequence for the following reasons:
- Our AI-based, out-of-band approach was developer-friendly, eliminating JavaScript and mobile SDK instrumentation penalties such as:
- Application deployment delays caused by QA and App Store validation cycles;
- potential security gaps across application versions/channels including web, mobile and API-based;
- user dissatisfaction from slow page loads.
- Automatic and continuous application discovery and visibility: The AI-based approach automatically discovered all applications, both current and newly deployed/updated, giving them visibility and the power to immediately turn knowledge into policy actions.
- Open, extensible platform: CQ Insight management allows the customer to quickly discover and prevent automated attacks while the REST-based APIs allows them to export the CQ botDefense findings to their existing security infrastructure for log analysis and reporting.
To learn more, come see us next week at FS-ISAC in Washington DC where we will present (Monday, Nov. 18 4:15PM-5:00PM) and demonstrate CQ botDefense (booth #60).
Not going to FS-ISAC? Check out this 5 minute video of CQ botDefense.
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.