Using NIST CSF to Reign in your API Footprint
As your digital transformation accelerates, it’s API volume and usage has accelerated in tandem. It is also very likely that your API security efforts have lagged behind your increase in API usage. Unlike other more mature areas of cybersecurity, the API security market is still relatively nascent and fractured. When people talk of API security, they mean lots of different things – securing the API endpoints, implementing web application firewalls (WAFs), bot management, API governance, or monitoring.
Like the market, conversations in your organization about API security are likely happening in a fractured manner, if at all. Without a way to focus the conversation, various development and operational teams may be taking different approaches to manage API security risks. It’s a step in the right direction, but proper API security and governance requires clarity and consistency. One approach being taken by more than 30 percent of U.S. organizations, is to the NIST Cybersecurity Framework as a way to develop a shared understanding of their collective cybersecurity risks.
As you build out your API strategy, the NIST CSF will help you gain a baseline of information about the APIs used across your organization, identifying potential gaps in the operational processes that support them. Your baseline can help you not only communicate where the organization is today but will also help define a publication process that helps to ensure your APIs – and the data flowing through them – are robust and secure.
Below are some questions aligned to the NIST CSF that you can use to help establish the baseline of your API operations while establishing future goals and plans. With this information in hand, you can begin to orchestrate the operational improvements that will help mitigate risks in existing APIs and with an eye towards consistency, reduce the risk in newly developed and deployed APIs. As your API strategy takes shape, it will be critical to implement a method of regular measurement and assessment so you can see how your API risk is changing as you work to achieve your API risk management goals.
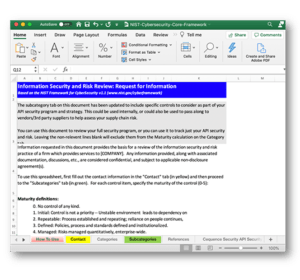
Additionally, we’ve also created an editable NIST CSF for APIs spreadsheet for you to download and use for your own internal assessment of your APIs.
Access the NIST CSF for APIs Assessment Tool Here
As you and your team go through the assessment, consider for each question your current state, what kind of risk it presents, what you want your future state to be and by when.
Asset Management:
- How many APIs do we have?
- What do the APIs do?
- Who are the API owners? Who manages them?
Business Environment:
- How were they developed? Which are Open Source vs. Custom built vs. Third-party?
- What applications are these APIs used by / associated with? Are they critical to business operations?
Governance:
- Is there a documented API vetting and publishing process?
- Which APIs are subject to legal or regulatory compliance? How do we monitor for vulnerabilities in your APIs?
- Which ones are not actively managed or monitored?
- Do they have traffic?
- How do we protect our APIs from malicious traffic?
Risk Assessment:
- Are there APIs with vulnerabilities?
- Are the vulnerabilities isolated to particular teams/products?
- What is the business impact if the APIs are compromised or abused?
- Do we have APIs that are not conforming to our API definitions?
- Do we have any hidden API headers, parameters or response codes?
- Are we seeing any malicious traffic? On which APIs?
- Is there API traffic that is outside of the expected? (coming from unexpected countries, for example)
- What is the overall risk? Is it trending up or down?
Risk Management Strategy:
- Are APIs included in our risk management processes?
Access Control:
- How do we manage authentication for our APIs?
- What is our process for modifying access rights for our APIs where appropriate?
- Do the APIs have appropriate levels of authentication?
Awareness and Training:
- Is API security a part of our on-going developer training and security evangelism?
- Are there teams with a high number of API vulnerabilities that require special attention and training?
- Do we need to implement an incentive structure to help strengthen our API security?
Data Security:
- Are our APIs exposing sensitive data or PII which could put us out of compliance?
Anomalies and Events:
- How do we monitor for malicious traffic on the APIs?
- How do we protect our APIs from malicious traffic?
- What is the process for analyzing API events to understand intent and targets?
- Have we established an alerting process for events detected on APIs?
Continuous Security Monitoring:
- How do we establish norms for traffic on APIs?
- How do we monitor for malicious traffic on APIs?
Detection Processes:
- How do we test and measure the effectiveness of our API monitoring?
No doubt we’ve missed a few questions, but surprisingly, we find that many of these questions are not easily answered, yet they are critical to understanding and ensuring your APIs, and your data, are secure.
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.