In case you missed the news, Cequence Security was born on November 13, 2018. That’s when we emerged from “stealth mode” and launched the new Cequence Application Security Platform (ASP), integrated CQAI analytics technology, and API Spartan service module. These components work as one tightly integrated software solution to stop advanced bot attacks targeting today’s hyper-connected organizations. The positive reaction to our launch has thus far exceeded our expectations.
But what about this name – Cequence Security?
We actually think it’s kind of a cool name. But aside from its inherent coolness, there is a logical reason we came up with that name. Pull up a chair, grab a beer, and let me explain.
The Cequence solution was designed to address two key customer requirements:
- A stronger security posture. This is enabled by first providing unmatched visibility into all applications deployed throughout the organization. From there, the solution accurately detects complex bot attacks that target a customer’s critical web, mobile, and API application services. Finally, the solution enables security teams to mitigate these attacks before they can achieve their objectives.
- Improved IT productivity and efficiency. Not many security vendors state this as a design objective. But we do. That’s because recent research indicates that as many as 3 million IT security positions will go unfilled over the next few years, simply because there aren’t enough skilled professionals to fill all of those roles. Therefore, we believe it is incumbent upon vendors to provide automation that can help minimize time wasted on manual tasks, and instead empower security teams with truly actionable information.
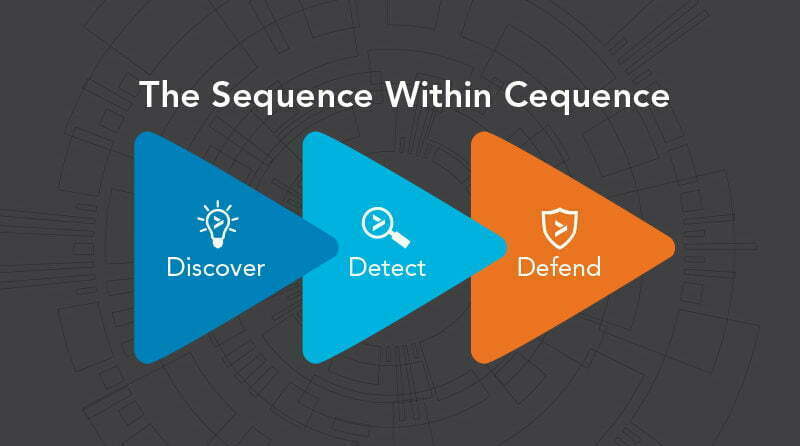
But what does this have to do with the name Cequence? Well, our patent-pending security solution automatically performs a sequence of 3 events:
- Discover – once it’s deployed, it discovers all web, mobile, and API application assets across the entire organization, on premises or in the cloud.
- Detect – continuously ingests and analyzes a copy of all relevant traffic flowing between clients and servers to detect malicious bot activity on the network.
- Defend – enables security teams to automatically apply various policy-based mitigation policies to immediately thwart the efforts of attackers.
So that’s the “sequence within Cequence.” But what’s really important is that this sequence of events also achieves our two design objectives: it immediately strengthens the security posture of the customer’s organization; and the AI-driven automation helps optimize the performance of IT security teams.
If you can spare 4 minutes, learn more by checking out this video:
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.