Retail cybercriminals have graduated from relatively quick, unsophisticated smash and grab-style attacks to playing the long game, spreading attacks out over the course of the year in preparation for a holiday season bonanza. This shift in tactics has come to light in the latest threat intelligence research from the Cequence CQ Prime Threat Research team in their 2023 Holiday Season API Security Report.
Over the years, Black Friday has become more than just a day – many “Black Friday”-type deals start at the beginning of November and run throughout the month including Small Business Saturday, Cyber Monday, and eBay’s Green Monday. Attackers have gone even farther, with the data showing that in some cases they prep all year long for a holiday season that ecommerce has come to dominate.
About the Data
What sets Cequence’s reports apart is that they are derived from anonymized, real-world attack data against customer production environments. This data is part of the Cequence API threat intelligence database, the largest such database in the world. The CQ Prime team uses this data combined with machine learning (ML) and threat prediction workflows to detect and mitigate API security threats for the world’s most attacked organizations comprising Fortune and Global 2000 companies.
With that, let’s dig into some of the report findings. You can download the entire report for free here.
The State of Threats and Bot Management Today
The data below are based on six months of anonymized traffic across all Cequence customers from June through November 2023.
- Malicious traffic came from 719 million unique IP addresses.
- Of 154 billion requests, 22 billion (14%) were automated (bot) requests and 19 billion (12%) were confirmed malicious requests. While these percentages may seem low compared to some seen in the news, they are predicated on the scope of traffic the numbers are sampled from. Cequence typically processes all API traffic for its customers, so the breadth of traffic is much larger than products that only examine login traffic to a particular instrumented web app, for example.
- The highest number of blocked requests in a single day was 216 million.
- There were 325 million malicious login or Account Takeover (ATO) attempts. ATOs remain one of the main tactics for adversaries, increasing more than 50% from the previous six-month period.
- More than 148 million different browser types (user agents) were observed. A relatively small percentage can be accounted for by operating system, device, and browser combinations – the overwhelming majority of the number represents attackers generating massive numbers of unique browser user agents as part of their schemes, which gives you an idea of the massive scale of attacks that today’s businesses are facing.
Pre-Holiday Cyber Assault: Attackers Lay Groundwork Ahead of Retailers’ Security Lockdown
The first threat analysis focuses on large consumer home and body product retailers. Gift card fraud is standard operating procedure for these types of companies – attackers use botnets to test large volumes of card and PIN numbers in hopes of finding a successful pair from which they can drain the card of funds. These types of attacks are fairly consistent throughout the year.
In 2023, Cequence noticed that other types of attacks came through at high volume starting early in the year. Since retailers are well known to lock down their networks during the holiday season as well as the fact that “Black Friday” can comprise a month’s worth of promotions for some retailers, the data suggest that attackers are laying the groundwork for their holiday attacks well in advance of the holidays.
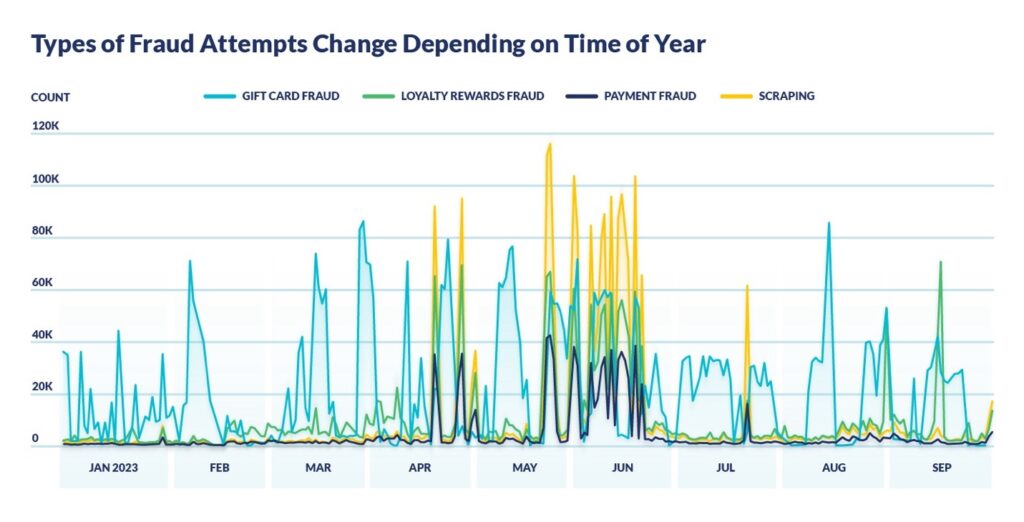
In the second half of the year, these companies noticed several types of attacks unrelated to gift card fraud happening in unison, as shown in the graph. While gift card fraud grew by 110% in the second half of the time period, scraping, loyalty card and payment card fraud increased by a collective average of over 700%. These types of attacks are correlated and spiked together because those parts of the website, applications, and associated APIs are related, especially as they pertain to attacks.
Bot Barrage: Combatting the Surge of Automated Line-Jumpers in High-Demand Retail Drops
You’ve probably read the stories about Taylor Swift tickets selling out instantly, or maybe you’re a sneakerhead trying to get the latest retro Jordans. You’ve probably run into bots trying to “jump the line” one way or the other, because it’s become a big problem for retailers that run flash sales or hype sales.
During these types of sales campaigns, attackers commonly use automated tooling to add large numbers of sneakers or other products to their cart in order to try and purchase as many in-demand items – either on sale or of limited availability – as possible. If successful, these bad actors can effectively corner the market and preventing sales to legitimate customers, and then sell these items elsewhere at a high markup.
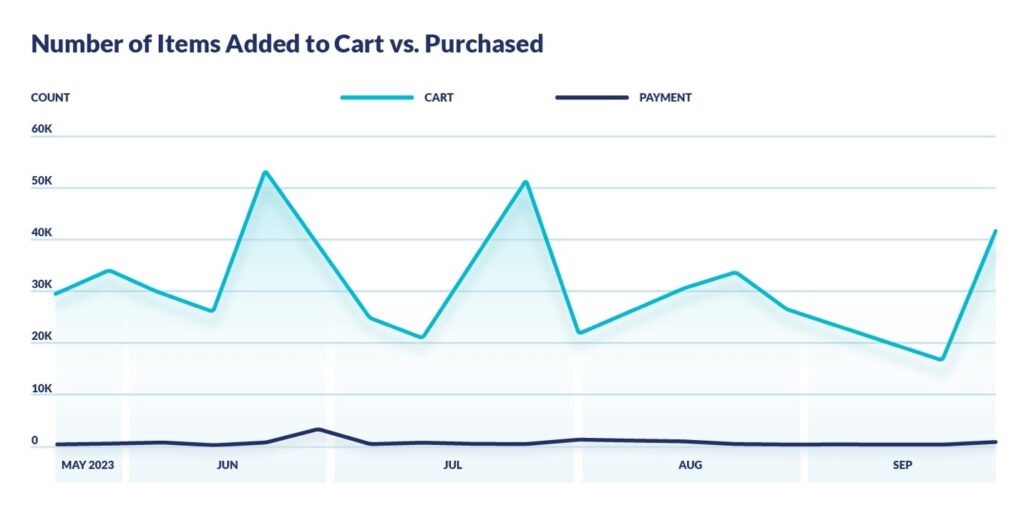
Cequence’s data shows that large numbers of products were added to carts, but few comparative purchases as the fraudsters were identified and prevented from purchasing. Add-to-cart spikes are correlated with product launches, as attackers attempt to monopolize limited-availability items.
Playing the Long Game: The Rising Threat of Trust-Building Account Takeovers
“Social commerce” retailers combine ecommerce with social media, leveraging user contributions to build community. Most online retailers encounter account takeover (ATO) attacks that peak during the holidays. ATO is an attack on legitimate existing online customer accounts, where criminals take ownership of the accounts for their own nefarious purposes. This year, Cequence noticed its social commerce companies encountering a different type of attack well before the holiday season began.
In this example, attackers attempted to create high volumes of valid accounts via standard APIs earlier in the year, hoping to use the time to build trust and cred in the market to increase social sharing and extend their reach, increasing the visibility of the products they’re selling over others’. The attacker’s automated tools enable them to create accounts and generate likes and subscribes to increase influence – but much faster and at a larger scale than legitimate humans could, crowding out the sales of legitimate users.
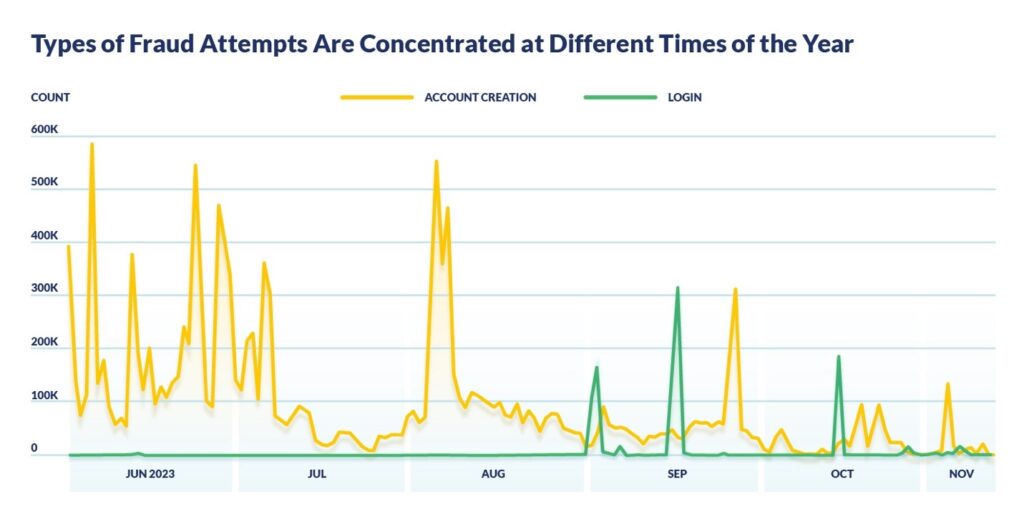
Fraudulent account creation attempts declined nearing the holidays, while basic account takeover tactics rose. While fraudulent account creation dropped 72% from the first half to the second half of the time period, account takeovers (ATOs) increased a staggering 410 times! This is due to the attacker changing tactics to those that require less runway and planning, like ATOs.
Cequence Customers Enjoyed a Smooth Black Friday
This Black Friday, Cequence customers were largely unaffected by bot attacks thanks to their ongoing efforts as well as Cequence innovations across engineering, customer success, and the CQ Prime Threat Research team. In fact, Cequence customers submitted the total fewest support tickets during the month of Black Friday (November) compared to the rest of the year, and tickets were 70% lower than last year.
Wrapping Up 🎁
2023 reminded us that attacks are constantly evolving, with new tactics and techniques designed to evade improving defenses. To protect against API threats like these, organizations need to adopt a comprehensive approach to their API security. They must discover and inventory all their APIs, ensure they’re in compliance with API specifications, and then identify and block attacks as they happen. Cequence can be your partner throughout the API security lifecycle and help protect your organization from existing and emerging threats.
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.