We are excited to announce the general availability of Cequence API Sentinel, a new API security service designed to give you continuous run-time visibility, shadow API discovery, risk analysis, and conformance assessment for all your APIs hosted on-premises and in public clouds.
If your organization delivers APIs to external parties, such as your customers or partners, you need a centralized place to help monitor the security posture of all your published APIs, detect any risks immediately, and respond proactively to mitigate risks of data exfiltration. Today, most organizations expose multiple APIs to external parties, published from different product teams, different application stacks, and following various DevOps and security procedures. Therefore, the first step in developing a mature API security program is to discover all APIs your organization delivers to external parties and analyze their risk postures.
API Sentinel facilitates the discovery process and delivers critical capabilities needed to understand your API security posture, including:
- Runtime API Catalog: Automatic discovery of all your APIs, including those you’ve published knowingly to 3rd parties, as well as unknown shadow APIs. API Sentinel integrates with your existing API Gateway and proxy deployments to rapidly provide this visibility.
- API Usage Analysis: Analysis of the usage of each API endpoint, including the countries, IP Addresses, and organizations from where usage is detected. Included are insights into headers, parameters, and response codes found in real-time usage, available with time-based filtering capability.
- Continuous Risk Scoring: A dynamic assessment of each endpoint’s risk posture, determined based on multiple factors, including the strength of access control mechanism used, detection of sensitive PCI or PII data, unencrypted communication, or non-conformance to the published OpenAPI definition.
- Shadow API Discovery: By uploading your OpenAPI definitions for your managed APIs, you can compare your APIs’ runtime behaviors with your published specifications. API Sentinel reveals the usage of shadow APIs and the usage of hidden methods, headers, parameters or response codes.
Delivered as a modern Kubernetes application, API Sentinel rapidly integrates into your application infrastructure and with API Management products such as Amazon API Gateway and Apigee, as well as with proxies or ingress controllers such as Nginx+ or Envoy.
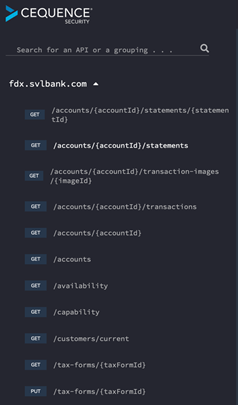
Runtime API Catalog
By integrating into your runtime environments via API Gateways or Proxies, API Sentinel discovers all your APIs in realtime usage, not just the ones you have published knowingly. A common source of risk is an inadvertent deviation in implementation across different environments, or from one version to another. This catalog discovers APIs hosted in multiple stages, such as dev and production, as well as multiple versions of the same API that may be exposed concurrently (e.g., v1 and v2).
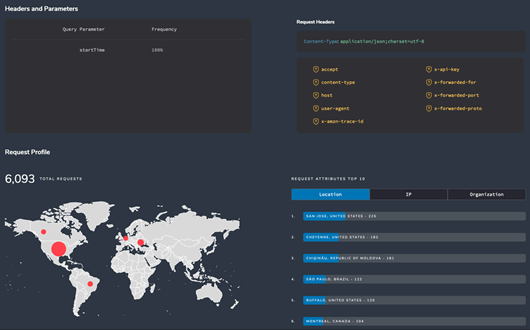
API Usage Analysis
API Sentinel provides you with usage analysis of each endpoint, including the countries, IP addresses, and organizations from where usage is detected. You can also find the headers, parameters, and response codes used in runtime, and filter based on different date ranges to see how usage changes over time.
Though an API specification may list a plethora of headers and parameters that can be accepted by the API, it is insightful to observe which ones are in active use, and from which regions, orgs or locations around the world.
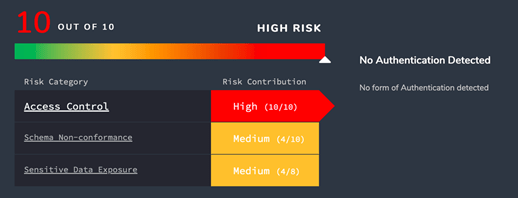
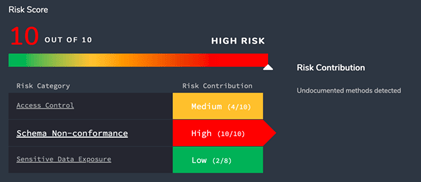
Continuous Risk Scoring
Across APIs spanning multiple functionalities and delivered from multiple teams, API Sentinel provides a unified dynamic assessment of risk, computed based on various risk factors. The Risk Score flags the particular risk categories that need to be investigated and remediated.
- Access Control – a quantitative assessment of the strength of authentication used for the endpoint. A high risk score is issued for unauthenticated endpoints, or those using weak forms of auth such as HTTP Basic Auth. A low risk score indicates a strong form of authentication, such as OAuth2/OIDC.
- Sensitive Data Exposure – a quantitative assessment of whether sensitive data is detected at runtime or if unencrypted communication is detected. The product comes pre-defined with definitions for PII and PCI, including US Social Security Numbers and credit card numbers. It can be customized to add custom expressions specific to your applications as well.
- Schema Non-Conformance – an indicator of whether the runtime usage conforms with the published OpenAPI definition. It is common to discover runtime usage of hidden headers, parameters, and response codes which weakens your security posture.
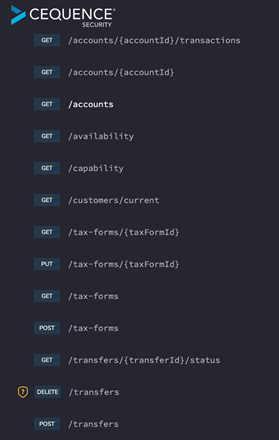
Shadow API Discovery
Shadow APIs are hidden endpoints that offer functionality unbeknownst to the organization. API Sentinel allows you to upload your OpenAPI definitions, so they can be compared with actual runtime usage. The differences between runtime usage and published specifications reveal unpublished endpoints, methods, or parameters, that may pose a significant security risk to the organization.
API Sentinel complements our Cequence API Spartan and App Firewall products, offering the industry’s only multi-threat API protection solution, unifying visibility and protection from malicious bots, and business logic abuse, and targeted vulnerability attacks.
API Sentinel can give you a better handle on the security posture of your APIs. Visit the product page for an overview and check out the explainer video and demo. You can also request a live demo of the product so we can walk you through the detailed capabilities.
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.