APIs used in connected vehicle systems offer points of entry for hackers and other malicious actors to exploit cars, trucks, telematics devices, and fleet management operators. In this blog you’ll learn what’s needed for an effective API security program to ensure vehicle safety and security for the entire API protection lifecycle.
The average vehicle has over one hundred million lines of software code used by dashboard-controlled air conditioning, audio, and navigation systems. In addition, software is involved in electronic control units (ECUs) that control engine functions, regulate braking behavior, and monitor the air conditioning system.
Connected Vehicles Rely on APIs For Basic Functionality
These systems are connecting to smartphone apps, along with third-party applications for diagnostic and maintenance scheduling, updating vehicles from the cloud, and autonomous driving. All this communication activity for connected vehicles is often glued together using thousands of APIs that allow the various systems to interact with each other to provide better functionality and performance.
Access and Control Vehicles by Exploiting API Security
This increasing use of APIs and 5G technology in the automotive industry present a growing attack surface for organizations and offer attackers a scalable and fully remote way to cause disruption and steal data.
Security researchers revealed the ability to access and control multiple vehicles by exploiting an API’s broken object-level authorization (BOLA). This is a common API vulnerability listed in the OWASP API Security Top 10: API1:2019 Broken Object Level Authorization
The researchers found that sending an API request, via a telematics service provider, with the VIN on a unique ID field enabled them to remotely start, stop, lock, and unlock vehicles. Exploiting other API flaws allowed the researchers to access PII (personally identifiable information) for owners of several global automobile brands.
While obtaining PII without permission is unacceptable for any customer, for the most expensive car brands, the ability to disclose owner information, from more high-profile individuals, with data that includes sales information, physical location, and customer addresses, could be particularly damaging to a business’s reputation.
This research shows that when it comes to API security, this industry is no different, and the OWASP API Security Top 10 vulnerabilities will also apply.
Fleet Management and Increased API Security Risk
Like car and truck manufacturers, fleet managers who oversee car leasing, commercial shipping companies and government agencies are now managing fleets that are more connected than ever and utilize data transmitted from telematic devices to improve services and revenues.
Similarly, this increased connectivity has introduced API-related cyber risks and the impact of a breach can be much more when compared to consumer’s connected vehicles. This is because fleet management can be considered as critical infrastructure with fleets transporting anything from food and vegetables to pharmaceuticals and natural resources.
Because fleet managers are using in-vehicle devices that connect with backend management systems and mobile applications, all enabled by APIs, they’re creating the opportunity for a large-scale attack via a non-secured API, similarly resulting in vehicle theft or data misuse.
The Problem with Private, Public, and Partner APIs
Thus, API security is crucial in the automotive industry because it protects the data and privacy of car owners and ensures that the car’s software and systems are secure from external threats ensuring products are safe and reliable.
The problem is that APIs have become so prevalent, and whether they are private, public, or partner APIs, some organizations may be unaware of all of the API’s that their vehicle control systems or applications are using.
Cequence Security has reported that over 50% of API’s are unknown or shadow API’s and roughly 31%, or 5 billion of 16.7 billion malicious transactions targeted unknown, unmanaged and unprotected APIs, commonly referred to as shadow APIs
What’s more even when all APIs are known and perfectly coded with no misconfigurations or compliance issues, attackers can still abuse them. Attacks on well-formed APIs are a common occurrence because the attackers exploit the same nonfunctional requirements that developers love about APIs – flexibility, speed and ease of use.
Ensure Vehicle Safety and the Protection of Information
So, what can be done to ensure vehicle safety, and the protection of driver and vehicle information caused by miscoded or abused APIs?
Because attackers do not adhere to a top 10 list, and perfectly coded APIs, whether open source or proprietary, are susceptible to attacks, API protection needs to begin with discovering, identifying, and inventorying your API footprint.
Once the API estate is known, continuous risk analysis can be performed to uncover and remediate sensitive data, authentication or specification non-conformance related coding errors for production and nonproduction APIs. This middle phase of the API protection journey also incorporates runtime attack detection. API protection for cars, trucks, telematic, and fleet management systems should include a focus on the OWASP API Security Top 10 list of potential vulnerabilities. This approach enables stakeholders to increase security posture by effectively identifying misconfigurations, threats, and risks related to vehicles.
Then, employing countermeasures such as real-time blocking or deception without the need for added third-party data security tools, combined with ongoing testing to ensure risky APIs do not go live make up the last phase.
API Security for Cars and Trucks
5G technology enables vast amounts of data being exchanged to monitor everything from driver safety to goods and asset tracking. All of this rich information exchange requires APIs to be secure, free of vulnerabilities and continuously monitored.
To combat the ever-present risk to vehicle and passenger safety, along with protecting customer data that is evident with APIs, requires a unified and integrated approach that works across the entire API protection lifecycle, across all API automotive system implementations.
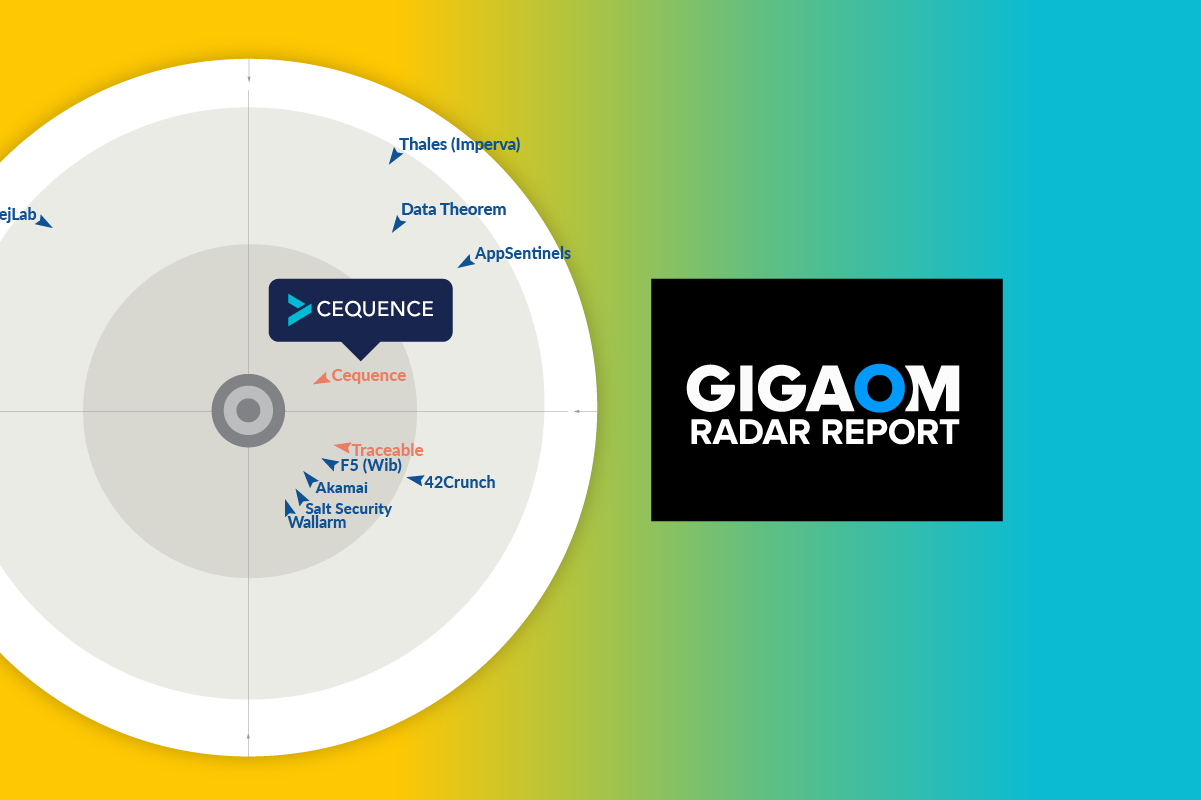
The good news is that Cequence Security has taken the approach of enabling API protection for the entire vehicle, consumer, and applications API lifecycle. With this approach APIs related to the operation of cars and trucks are continuously discovered using machine learning-based attack surface discovery. Pre-defined, imported or dynamically generated API tests helps security and development teams quickly uncover and remediate API vulnerabilities including OWASP API Top 10 risks. Vulnerabilities are detected with enhanced detection capabilities and layered with deep contextual analysis. The solution leverages monitoring, profiling of APIs associated with vehicles, consumers, and applications to detect API-related automotive threats.
The Cequence approach helps enable a collaborative effort for connected vehicle API security that includes developers, application owners and the security team to accomplish the following:
- Outside-in discovery: Gain an understanding of your public-facing API footprint for your connected vehicles to see what an attacker may see.
- Inside-out inventory: Complement an external view of your APIs in your network and related resources with a comprehensive inside-out API inventory, including all existing APIs and connections.
- Compliance monitoring: Continually analyze existing and new APIs to keep them in compliance with specifications such as the OpenAPI specification and ensure high API coding quality, consistency, and governance.
- Threat detection: Even perfectly coded APIs can be attacked, so it’s critical to continuously scanning your entire API inventory for threats, including your API traffic for subtle business logic abuses and malicious activity that has not yet been observed.
- Threat prevention: It’s critical to be able to respond quickly and natively with countermeasures such as alerts, real-time blocking and even deception, without the need for added third-party data security tools.
- Ongoing API testing: Integrate API protection into development to complement API security efforts defined by shift left efforts within the organization, so risky code doesn’t go live.
Unified API Protection is different from fragmented or incomplete API protection offerings because it’s a methodology designed to account for multiple types of risk, across every phase of the API protection lifecycle. In the automotive industry, security teams deploying Cequence Unified API Protection (UAP) enable their organizations to help ensure vehicle safety, and customer data.
The Cequence UAP creates a complete runtime inventory of all managed and unmanaged APIs, known and previously unknown. Discovered APIs risks are flagged for remediation while sophisticated threats are detected and mitigated in real time. The result is complete protection from API threats that cause data loss, theft, fraud, and business disruption.
Overall, API security is a critical issue for the automotive industry and connected vehicles, and manufacturers need to take it seriously to protect their customers and ensure that their products are secure, safe and reliable.
Get Started Today with the Cequence Unified API Protection Solution.
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.