It’s no secret that APIs are an invaluable tool for application developers who are tasked with doing more with less.
Driven by mobile device ubiquity and the move towards modular applications where APIs are used as the foundational elements of the application business logic, organizations are using APIs for many things, including to facilitate interoperation with other applications, reduce development time and extend functionality.

Source: SmartBear State of the API, 2019 Report
Unfortunately, APIs are commonly used for automated attacks against public facing applications, as shown in the Prying-Eye vulnerability attackers. According to Gartner, by 2021, 90% of web-enabled applications will have more surface area for attack in the form of exposed APIs rather than the UI, up from 40% in 20191. By targeting the API instead of scripting a form fill, a bad actor can leverage the same benefits of ease of use, efficiency and flexibility that APIs bring to the development community.
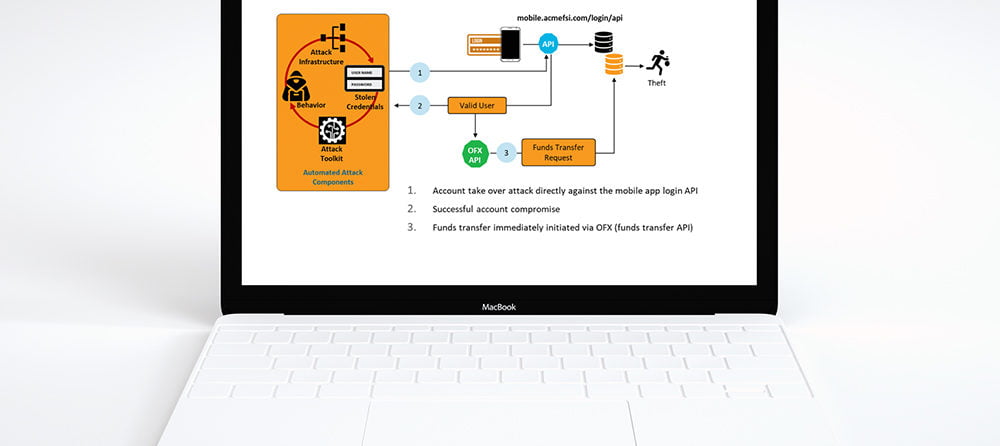
An example of an API-based attack against a financial services mobile application is shown in the image below. Bad actors decompiled the mobile application to (1) discover the account login APIs. An automated attack was then executed against the login API (2) and if successful the bad actors attempted to commit financial fraud by transferring funds (3) across the Open Funds Transfer (OFX) API.
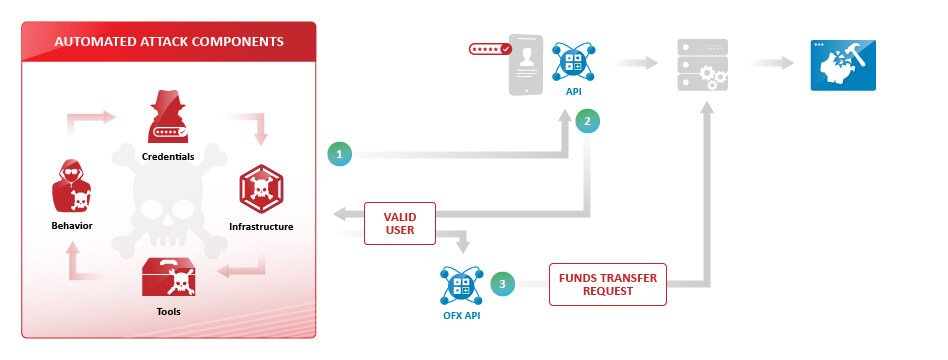
Bad actors will deconstruct the mobile applications which are heavily reliant on APIs to then launch an automated attack. For example, a financial services customer was able to detect and block an account takeover attack that targeted the mobile application account login. The bad actor, if successful, would then try to transfer funds using the OFX API.
Cequence was able to detect and block this ATO attack using our intelligence-based approach that allows API Spartan to discover all application endpoints – API, web, mobile – protecting them from automated attacks. Our unique approach to detecting and preventing automated attacks eliminates application instrumentation and mobile SDK penalties that may result in application deployment delays, security gaps and user dissatisfaction. An added benefit is consistent protection against all manner of automated attacks – ATO, fake account creation, content scraping and more – regardless of which application channel is being attacked.
Learn more:
1) Gartner, API Security: What You Need to Do to Protect Your APIs, August 2019
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.