We recently joined CNCF for two specific purposes. First off, our application is a distributed, containerized architecture that runs in a Kubernetes environment and as such, we want to support the project as a whole. The second reason we joined is to help educate customers on ways in which Kubernetes security can be embedded into their containerized application development workflows.
Kubernetes, a CNCF project, is an orchestration platform for automating deployment, scaling and management for containerized applications. Although there are other competing technologies like Apache Mesos and Docker Swarm, Kubernetes has emerged as a leader and the container world is settling in for it to become standard in all environments, be it on premise or in the cloud. Enterprises are adopting Kubernetes to enable their application teams to move away from the monolithic application development approach towards a methodology that incorporates smaller micro-applications and services. This empowers the application teams to adopt a more iterative and agile development methodology, resulting in more rapid deployment of new applications and updates to existing applications.
As a platform with rich computing, networking and storage capabilities, Kubernetes can be fairly complex to implement. Enterprises can choose to implement Kubernetes themselves, or they can choose a commercial distribution such as RedHat OpenShift, Pivotal Container Service (PKS) and several others. For public cloud-based deployments, enterprises can use Google Kubernetes Engine, Amazon Elastic Container Service (EKS) and Azure Kubernetes Service. Regardless of which Kubernetes infrastructure deployment direction an enterprise takes, security remains a critical consideration before they make it available to their application teams.
The first step towards protecting your Kubernetes deployment is to ensure that the platform itself is secure. This includes keeping up with the vulnerabilities of the platform, firewall rules to limit access to the Kubernetes infrastructure, etc. These security responsibilities are handled by the platform providers in the case of commercial and managed environments. Moving up the stack, the next set of responsibilities to consider is security of the containers themselves through role-based access control segmentation and so on. These responsibilities can be addressed by container security and compliance companies such as Twistlock, Aqua and StackRox.
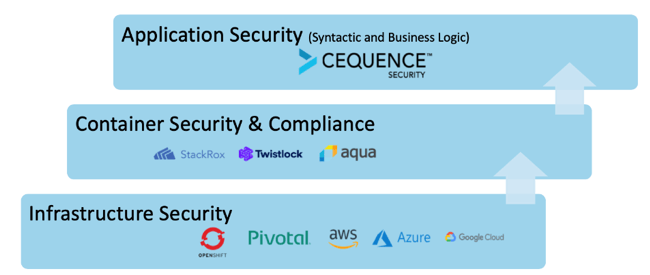
Once you secure the infrastructure and containers, the next step is to address the application level security challenges, which are the same, regardless of where the application is deployed – on-premises or in the cloud. The applications are prone to two types of attacks; syntactic abuse such as SQL injection attacks, cross-site scripting, buffer overflow, and business logic attacks which includes account take over, fake account creation, fake likes, shopping bots and more. The challenge for security teams is that they cannot keep pace with the speed that the applications teams are moving, resulting in delays or worse yet, degradation of the overall security posture.
Application security is where we can help. Our customers understand that we protect their external facing application attack surface that is constantly changing in the CI/CD world of Kubernetes. There are three ways that Cequence provides peace of mind to short-staffed security teams:
- “Baked-In” Security: When monolithic applications are broken down into smaller microservices, the application developers are free to choose different application platforms. The security
teams have the responsibility to protect these heterogeneous application environments; Java, Node.js, PHP, etc. to name a few. Enabling a unified and consistent application security posture across these heterogeneous environments is a significant challenge. Yet forcing the application teams to implement any kind of security injects friction and delay into the development process. Cequence Application Security Platform addresses both of these challenges by operating completely inside the Kubernetes environment, requiring no application instrumentation while protecting all applications automatically as they get rolled out. Security can operate at the speed of the application development team. - Continuous Application Discovery with Continuous Delivery: The ingress controller in Kubernetes is designed to manage access to applications from the outside world. The same IP and port can be used to serve multiple applications and their versions. Identifying the application just by their IP and port is insufficient to protect them. As new applications are on-boarded, the attack surface for the enterprise increases and its possible that each unique application is prone to different vulnerabilities. The first step to providing security is to automatically discover any new application that is being deployed. Cequence continuously discovers new applications as they are deployed, allowing the security teams to focus on the overall security posture, without worrying about which web, mobile or API-based endpoint developers are exposing.
- Consistent Application Security Attack Protection, Regardless of Deployment: Cequence provides a consistent and unified way to provide application security wherever the applications reside; on premise, in the cloud or hybrid. It is a logical extension to protect all the applications in the Kubernetes environment as well. To enable unified security across any deployment location, Cequence eliminates the need for application instrumentation to protect against business logic attacks, which makes it very easy to embed application security into the CI/CD process in Kubernetes environments. In contrast, traditional business logic abuse/bot detection vendors can introduce delays by requiring JavaScript injection into web applications or re-compiling mobile endpoint applications with an SDK.
We are excited to join CNCF so that we can contribute and collaborate with other members that share our vision of application security. We seamlessly integrate our capabilities with Kubernetes to help ease the transition for customers adopting cloud-native architectures, no matter where they are running, on-premise, public cloud or hybrid environments.
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.